
NUMEN’s on-chain monitoring has detected a price manipulation attack on the BonqDAO on the Polygon chain on Feb-01-2023 at 6:29:18 PM UTC. As a result, 113,813,998 WALBTs and 100,000,000 BEURs worth approximately $88 million were lost.
Attacker address: 0xcAcf2D28B2A5309e099f0C6e8C60Ec3dDf656642
Attacker Contract: 0xED596991ac5F1Aa1858Da66c67f7CFA76e54B5f1
Attacker transactions:
- 0x31957ecc43774d19f54d9968e95c69c882468b46860f921668f2c55fadd51b19.
- 0xa02d0c3d16d6ee0e0b6a42c3cc91997c2b40c87d777136dedebe8ee0f47f32b1
Attack Analysis
The attacker first verifies that the ‘withdrawAllTokens’ function operates correctly with a small number of tokens and then transfers a small quantity of TRB and WALBT to the attack contract in preparation for the subsequent attack.
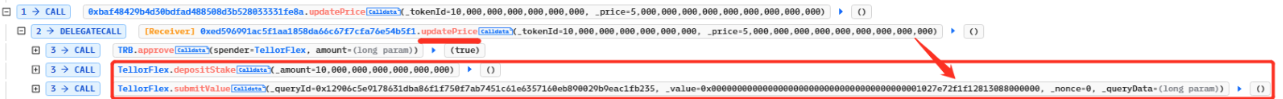
The attacker fulfils the criteria for updating the price by adding a pledge deposit to the TellorFlex contract, thereby changing the price to 50000000000000000000000000000000.
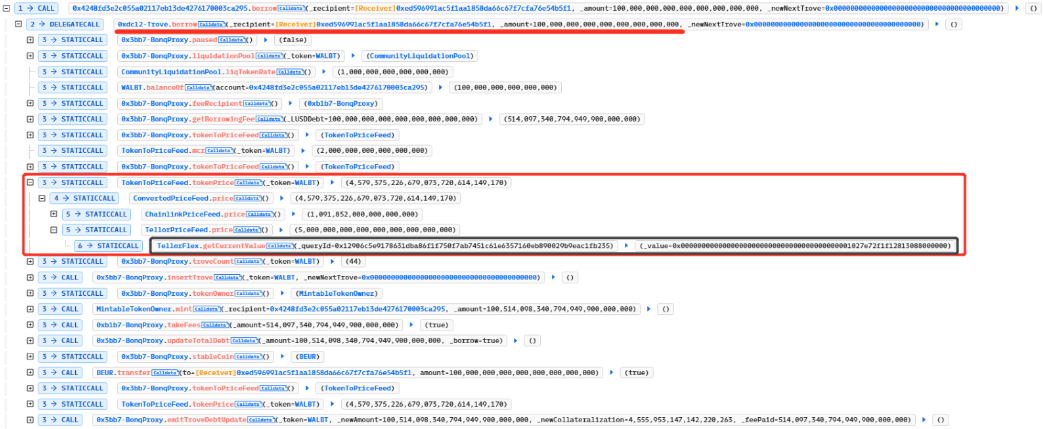
The attacker then obtains a loan by invoking the borrow method. As the borrowing cost is obtained from TellorFlex.getCurrentValue, the attacker has tampered with this value, resulting in an inflated cost. Consequently, the attacker was able to secure a large loan.
Core of the Vulnerability
The key issue is in the submitvalue of the contract
https://polygonscan.com/address/0x8f55d884cad66b79e1a131f6bcb0e66f4fd84d5b#code
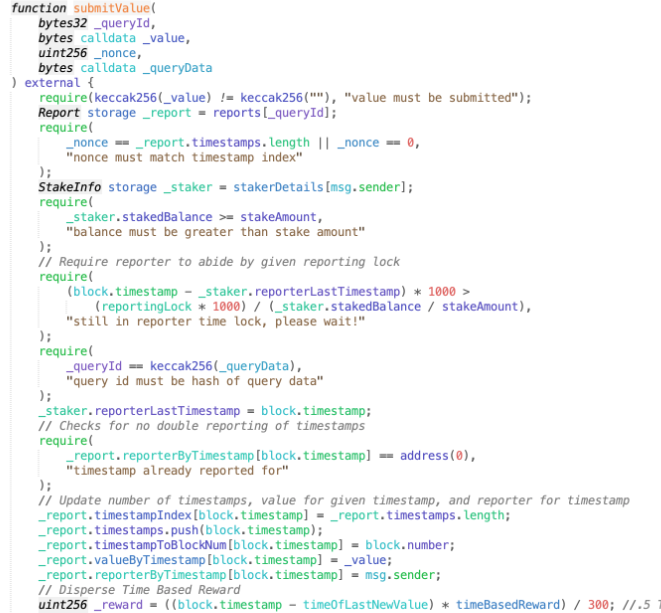
In the previous step, the attacker had already pledged the asset by calling depositStake (pledging 10 TRBs). As a result, they are able to send an offer to the prophecy machine in this step. The more pledges made, the more frequently the offer will be updated.
Next, we examine the price query.
https://polygonscan.com/address/0xa1620af6138d2754f7250299dc9024563bd1a5d6#code
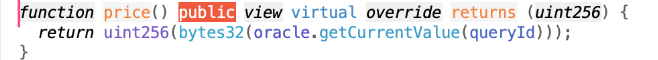
https://polygonscan.com/address/0x8f55d884cad66b79e1a131f6bcb0e66f4fd84d5b#code
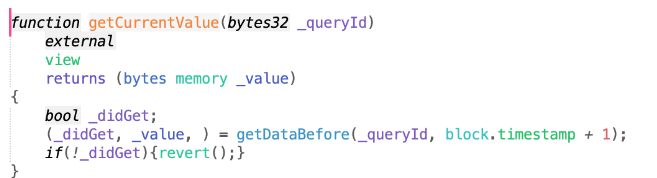
Follow up to getDataBefore
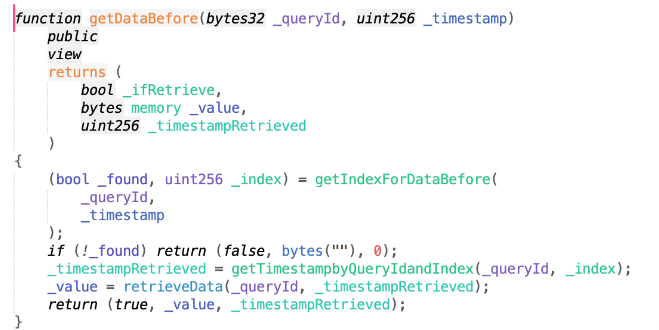
Next, consider the functions getIndexForDataBefore, getTimestampbyQueryIdandIndex, and retrieveData.
queryId is a constant and the first step is to determine the index based on the timestamp as there may be multiple quotes recorded for that time. Then, using queryId, the price is obtained and the return value matches the second parameter of the previous submitValue call:
In hexadecimal: 0x00000000000000000000000000000000000000001027e72f1f12813088000000
In decimal: 500000000000000000000000000000000000.
Therefore, as the TellorFlex contract is quoteable, the ability to quote is dependent on the user pledging an asset. By pledging 10000000000000000000, the user gains the opportunity to quote once every 12 hours. The quotation was then executed through the TellorFlex.submitValue function.
Reproducing the Attack
EXP
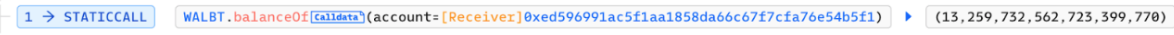
EXP source code link:
https://github.com/numencyber/SmartContractHack_PoC/blob/main/BonqDAO_exp.sol
Test Result
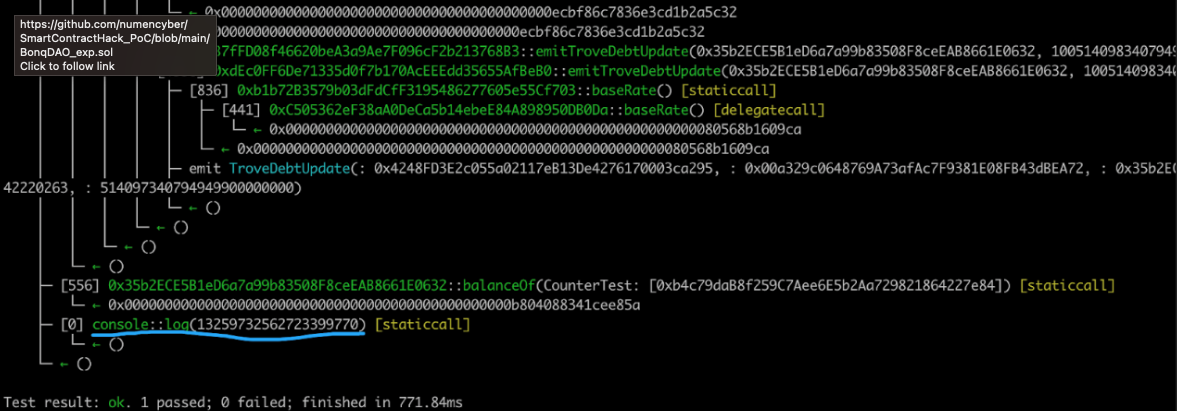
Summary
NUMEN Labs reminds project owners that it is important to have strict control over token prices. When multiple feeds are combined in a single calculation, it is important to consider the fairness of the price calculation and the risk of a single feed having too much control.
If you wish to audit and ensure that your projects are free from exploits such as these, please reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!


