
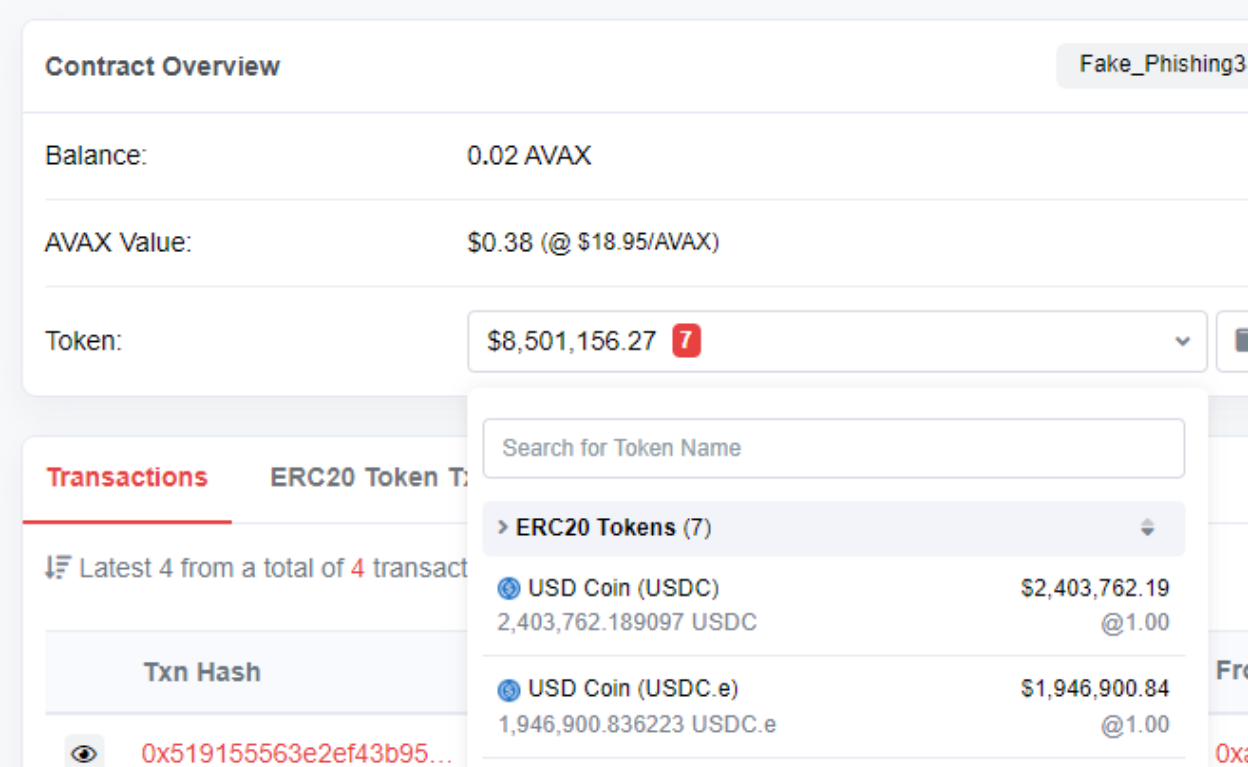
According to Numen’s on-chain monitoring, on Feb 16th, 2023 at 07:16:54 PM +UTC, the Platypus Finance project on the Avalanche network was hit by a flash loan attack due to a logic issue in the emergencyWithdraw function of the MasterPlatypusV4 contract, resulting in a total loss of 8.5 million US dollars. The stolen funds are currently in the possession of the hacker’s contract address.
Hacker address: https://snowtrace.io/address/0xeff003d64046a6f521ba31f39405cb720e953958
Hacker contract address: https://snowtrace.io/address/0x67afdd6489d40a01dae65f709367e1b1d18a5322
Attack transaction: https://snowtrace.io/tx/0x1266a937c2ccd970e5d7929021eed3ec593a95c68a99b4920c2efa226679b430
Attack Analysis
The attacker first borrowed 44 million USDC from Aave via a flash loan, and then used the borrowed USDC to call the deposit function of the Pool contract to stake it, obtaining 44,000,100,592,104 lp tokens.
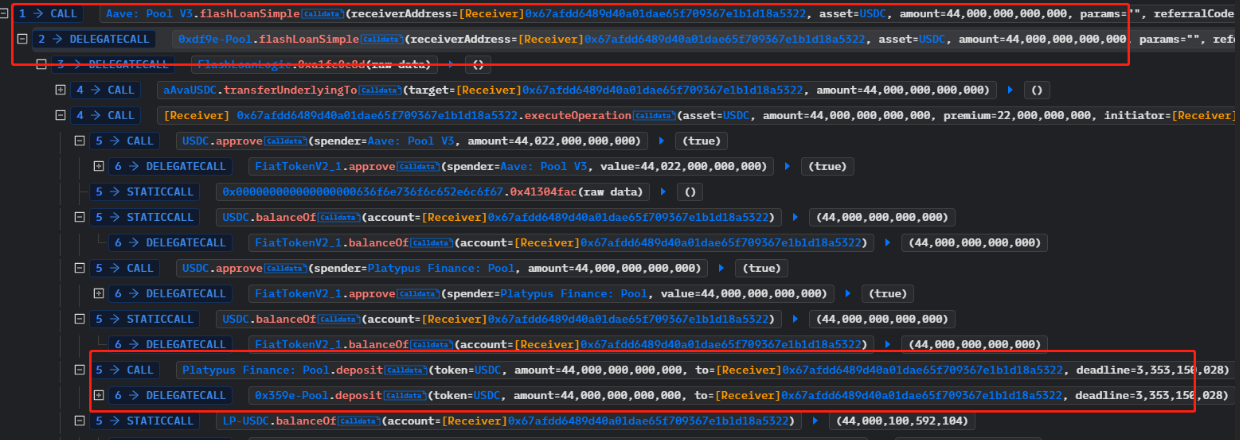
The attacker then staked the obtained lp tokens by calling the deposit function of MasterPlatypusV4, and further utilized the borrow function of the PlatypusTreasure contract to take out a loan. The borrowing limit of PlatypusTreasure is up to 95% of the staked amount, and the attacker borrowed 41,794,533,641,783,253,909,672,000 USP.
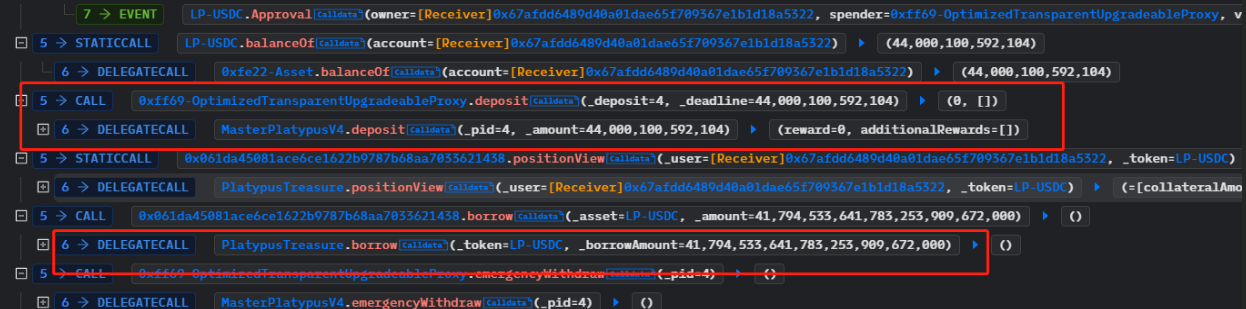
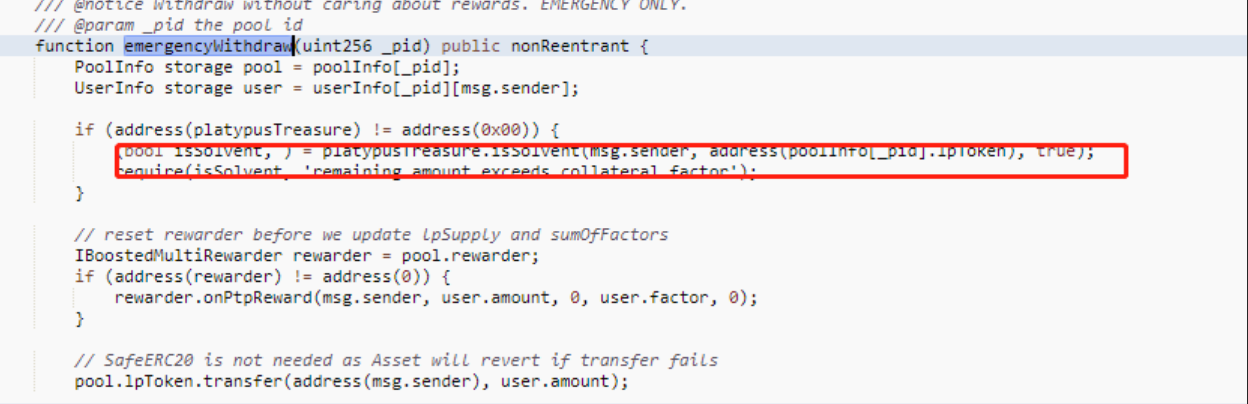
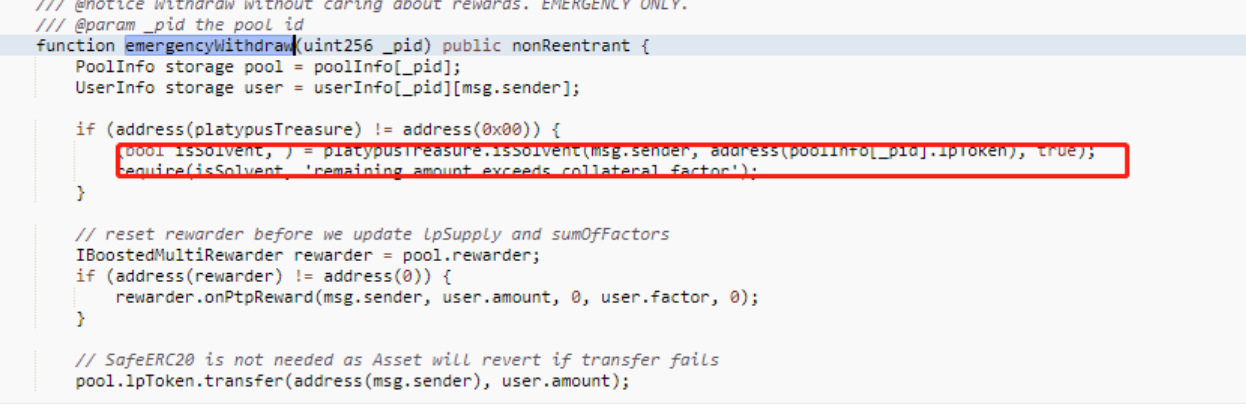
After completing the borrowing, the hacker called the emergencyWithdraw function of MasterPlatypusV4 to withdraw the staked lp tokens. As the borrowed amount did not exceed the maximum limit in the code, the isSolvent function returned true, allowing the hacker to withdraw the stake.
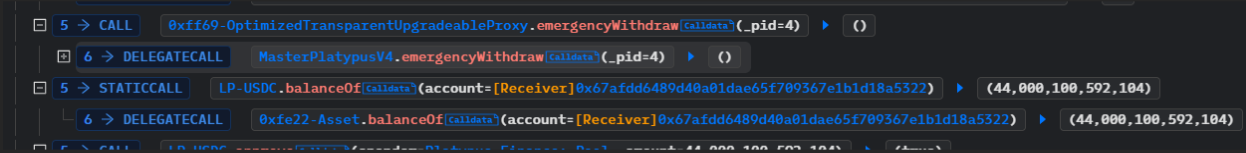
The hacker’s funds are currently still in their attack contract and have not been transferred elsewhere.
Core of the Vulnerability
Proxy: https://snowtrace.io/address/0xff6934aac9c94e1c39358d4fdcf70aeca77d0ab0
MasterPlatypusV4: https://snowtrace.io/address/0xc007f27b757a782c833c568f5851ae1dfe0e6ec7
The main vulnerability is in the emergencyWithdraw function. When a user makes an emergency withdrawal, the function does not check the user’s status in repaying their borrowed funds, allowing the hacker to directly withdraw the stake.
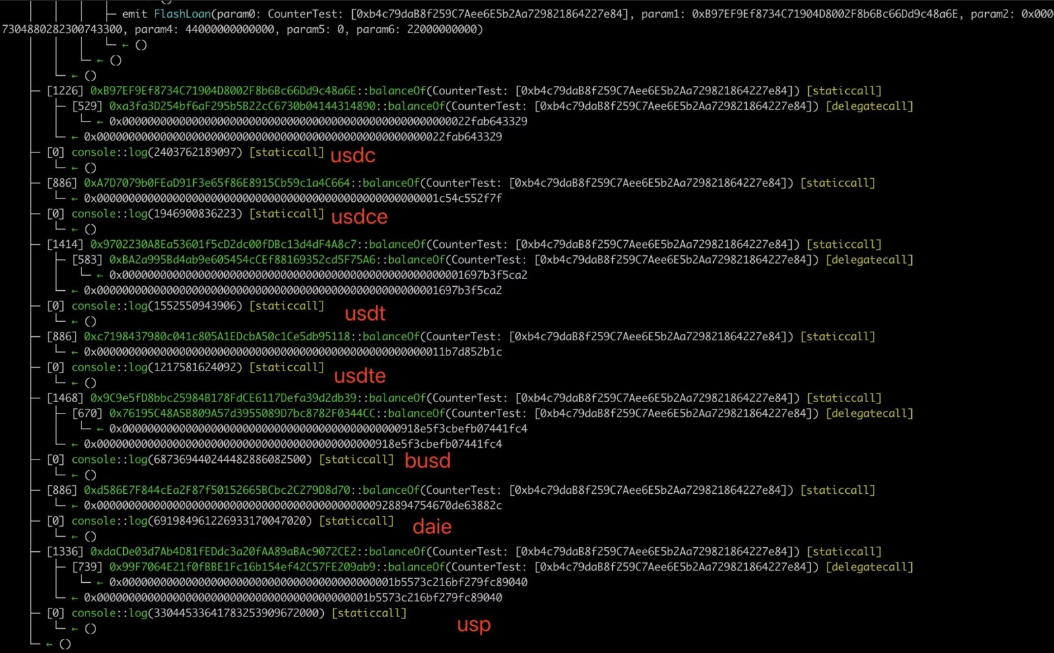
POC Reproduction
Link: https://github.com/numencyber/SmartContractHack_PoC/tree/main/PlatypusDefiHack
Results:
Conclusion:
Numen Cyber Labs reminds project teams to conduct strict checks on the status of borrowed funds and the amount borrowed when staking and borrowing in the contract. Multiple security audits should be conducted before the contract is launched to ensure that risks are eliminated as much as possible off-chain.
If you wish to audit and ensure that your projects are free from exploits such as these, please reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!


