
On 13 March 2023 at 08:56:35 AM +UTC, DeFi lending protocol Euler Finance experienced a Flash Loan Attack.
Euler Finance is a protocol that operates as a permissionless lending protocol. Its primary goal is to facilitate lending and borrowing of various cryptocurrencies for users. The UK-based tech startup utilizes mathematical principles to develop non-custodial protocols on Ethereum and other blockchain networks, with a focus on achieving high performance.
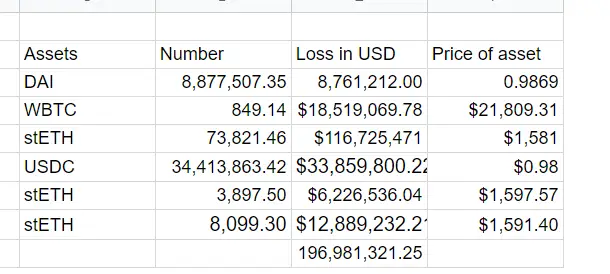
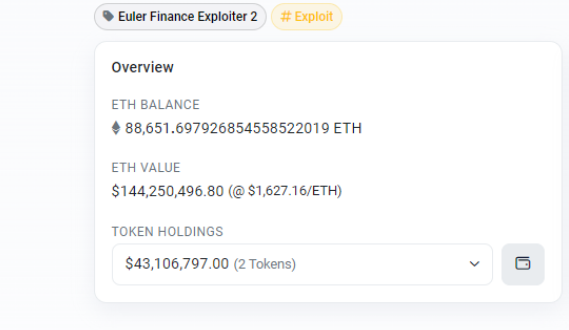
Based on on-chain data analysis, the attacker has successfully executed multiple transactions resulting in the theft of approximately $196 million, making it the largest hack of 2023 thus far. Stolen assets include several million worth of DAI, USDC, Staked Ether (StETH), and Wrapped Bitcoin (WBTC).
The breakdown of the stolen assets are as follows:
Detailed Analysis
The attack was possible due to a lack of liquidity checks in the donateToReserves function of the Etoken. The attacker executed multiple calls with different currencies to generate profit, resulting in a massive loss of $196 million across six different tokens. Currently, the funds remain in the attacker’s account.
The attacker’s address is: https://etherscan.io/address/0xb66cd966670d962c227b3eaba30a872dbfb995db
The attacker’s contract address is: https://etherscan.io/address/0x036cec1a199234fc02f72d29e596a09440825f1c
One of the attack transactions can be found here: https://etherscan.io/tx/0xc310a0affe2169d1f6feec1c63dbc7f7c62a887fa48795d327d4d2da2d6b111d
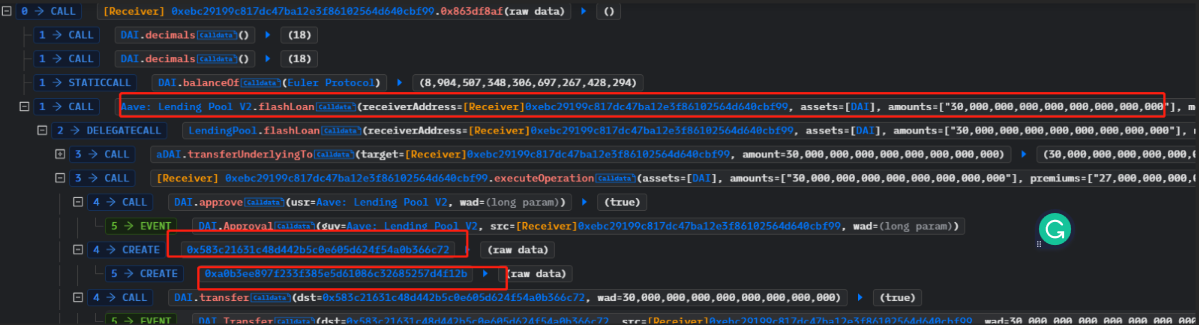
1. The attacker first borrowed 30 million DAI through a flash loan from Aave and then deployed two contracts: one for lending and one for liquidation.
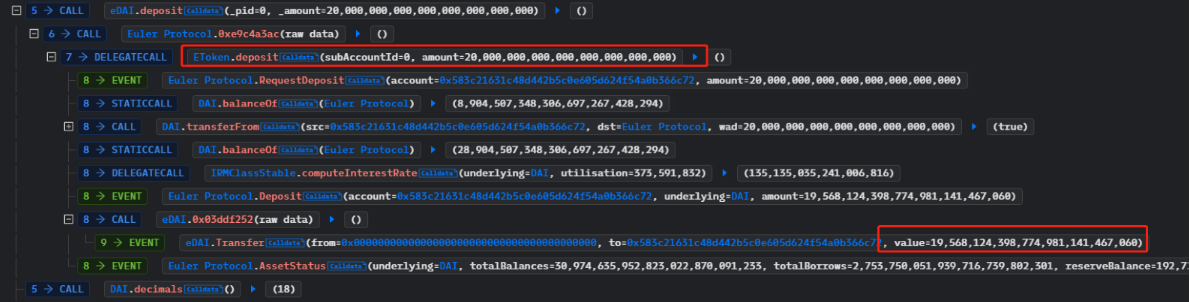
2. The attacker then called the deposit function and pledged 20 million DAI to the Euler Protocol contract, receiving 19.5 million eDAI in return.
3. The Euler Protocol allows users to borrow up to 10 times their deposit by calling the mint function. The attacker leveraged this capability to borrow 195.6 million eDAI and 200 million dDAI.
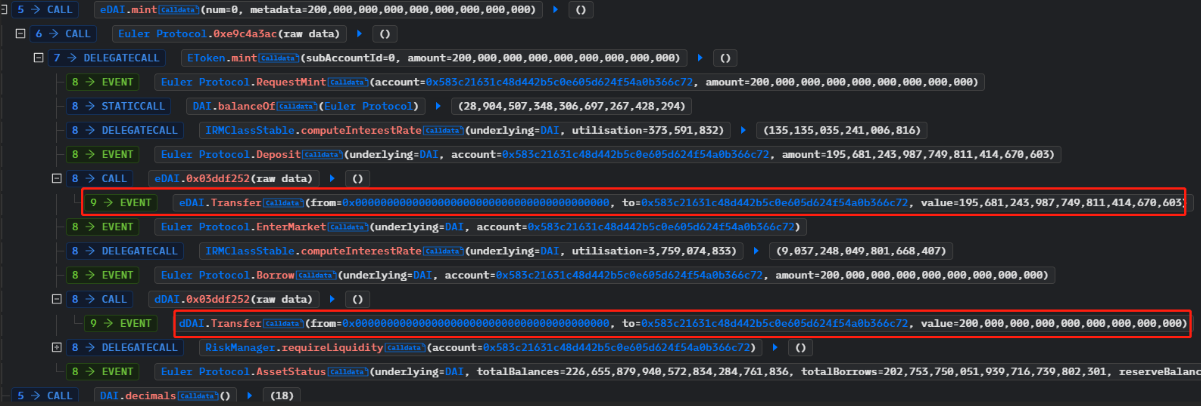
4. The attacker called the repay function using the remaining 10 million DAI borrowed through the flash loan to repay their debt and destroy 10 million dDAI. They then proceeded to call the mint function again to borrow 195.6 million eDAI and 200 million dDAI.
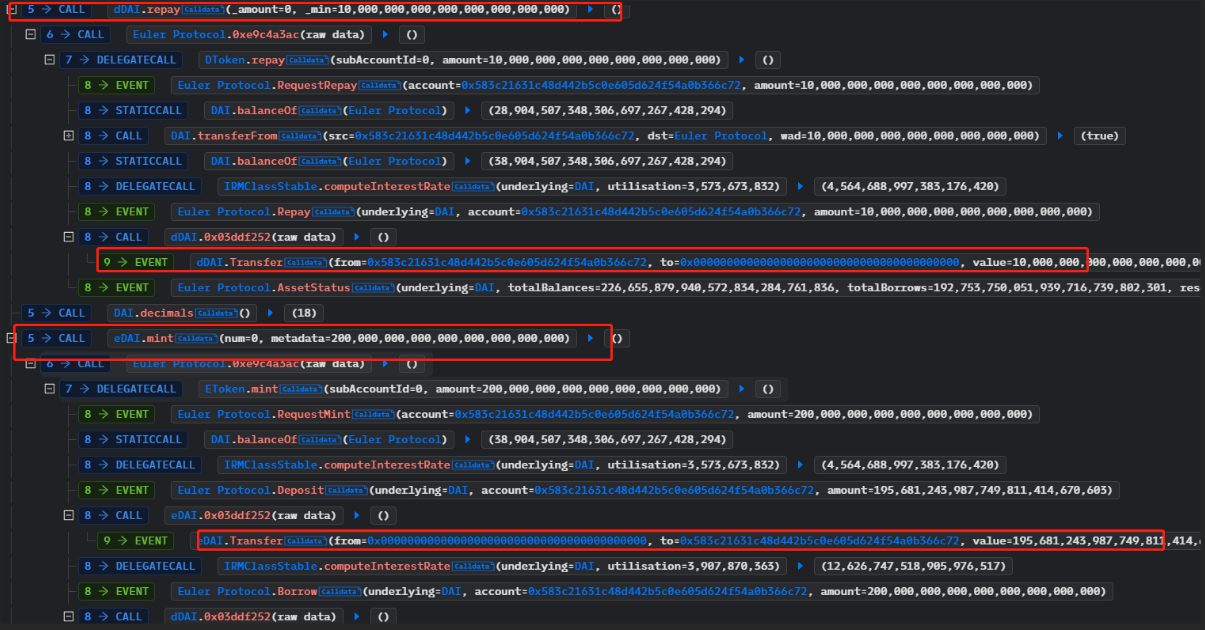
5. The attacker then called the donateToReserves function and donated 10 times the amount needed to repay their debt, sending 100 million eDAI. They then called the liquidate function to initiate the liquidation process and obtained 310 million dDAI and 250 million eDAI.
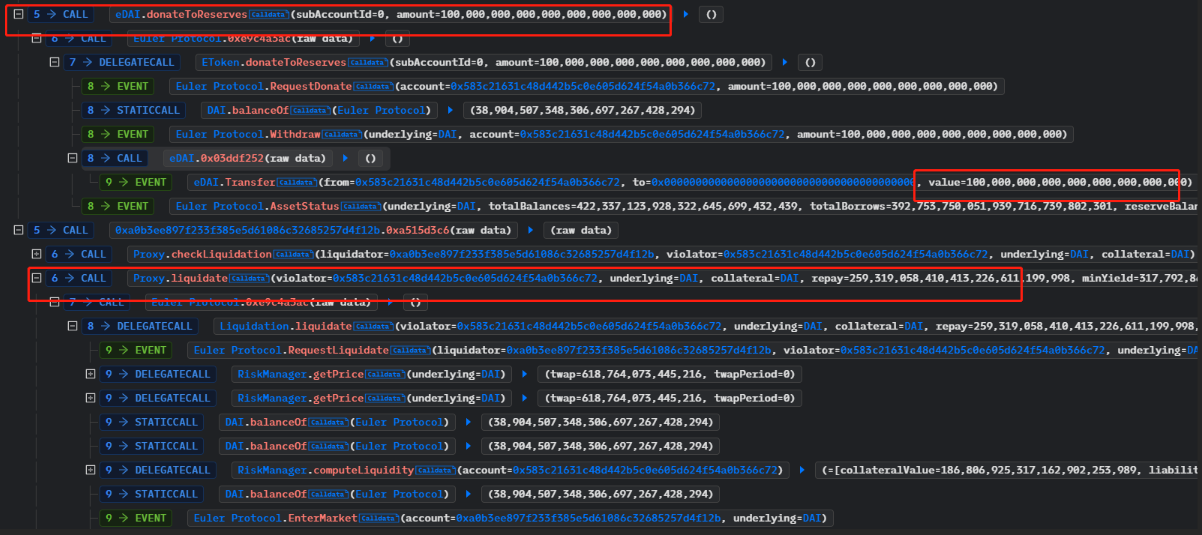
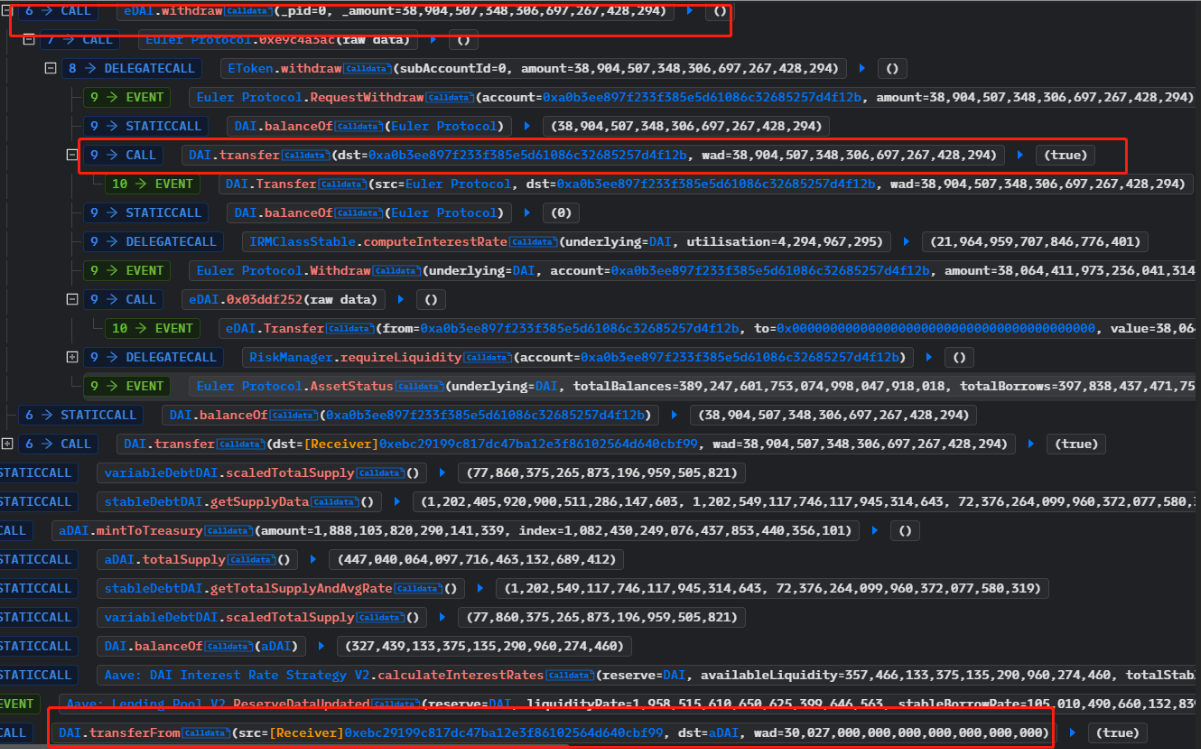
6. The attacker called the withdraw function and obtained 38.9 million DAI, which they used to repay the 30 million DAI borrowed through the flash loan. They profited 8.87 million DAI from the attack.
Core Vulnerability
First, let’s take a look at the donateToReserves function, which is where users become vulnerable to liquidation.
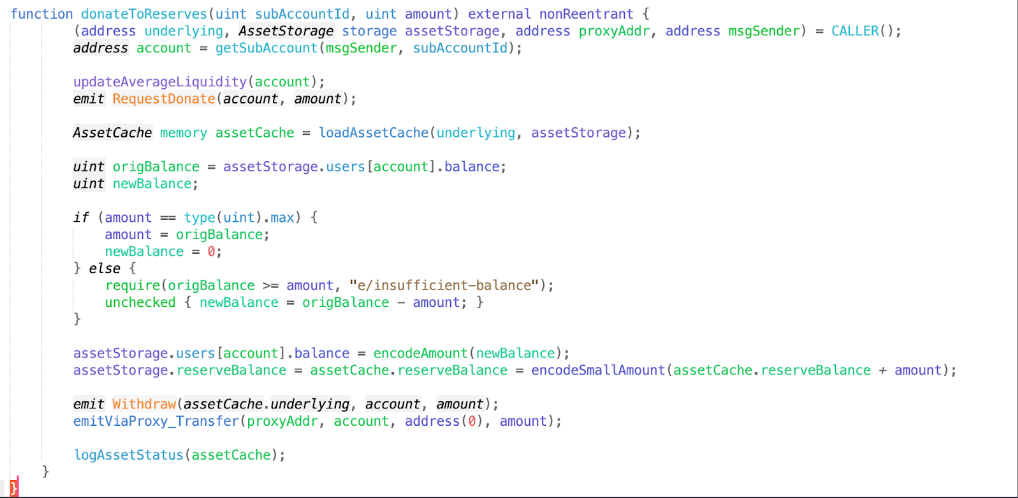
Comparing the donateToReserves function to the mint function in the diagram below, we can see that a key step, checkLiquidity, is missing from the donateToReserves function.
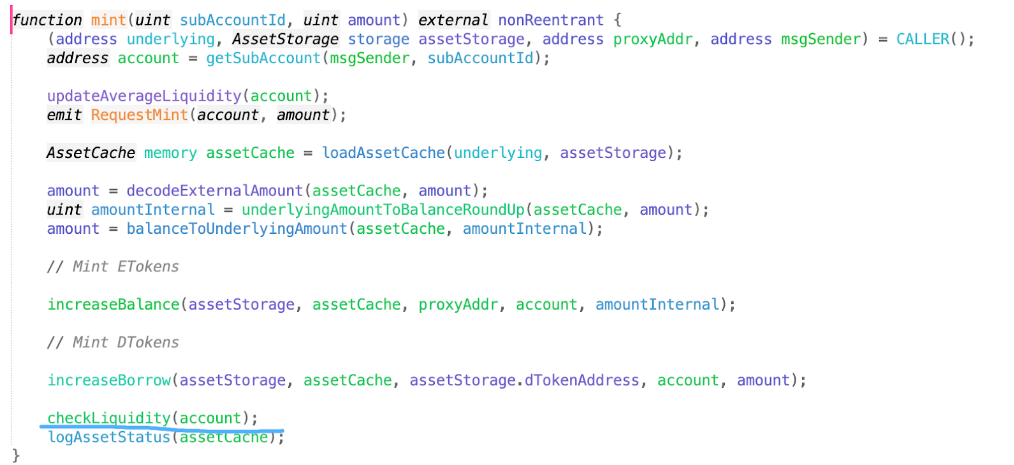
Next, we followed up and examined the implementation of checkLiquidity. We discovered the Call InternalModule function, which calls the RiskManager to check and ensure that Etoken > Dtoken for the user.
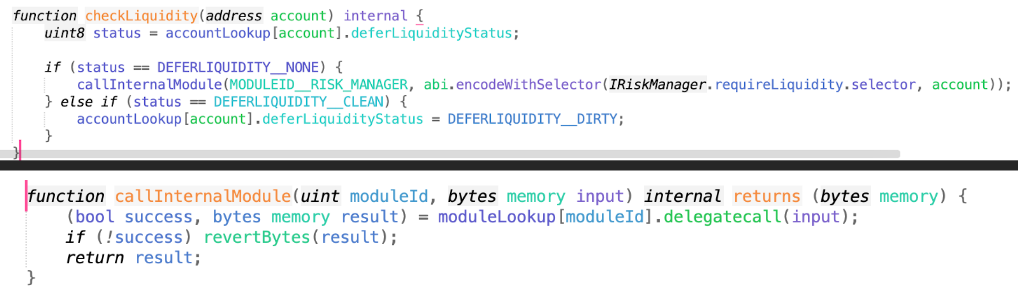
It is necessary to check the user’s liquidity each time an operation is performed by calling checkLiquidity. However, the donateToReserves function does not execute this operation, allowing users to first put themselves in a state of liquidation through certain functions of the protocol, and then complete the liquidation.
Attack Reproduction
The Numen Cyber Lab’s team has managed to reproduce the attack.
You may find out more details on the PoC at https://github.com/numencyber/SmartContractHack_PoC/tree/main/EulerfinanceHack
Official Updates on the Attack
Euler Finance have confirmed the attack on their official Twitter (@eulerfinance) and have stated that they are currently collaborating with security professionals and law enforcement to address the issue.
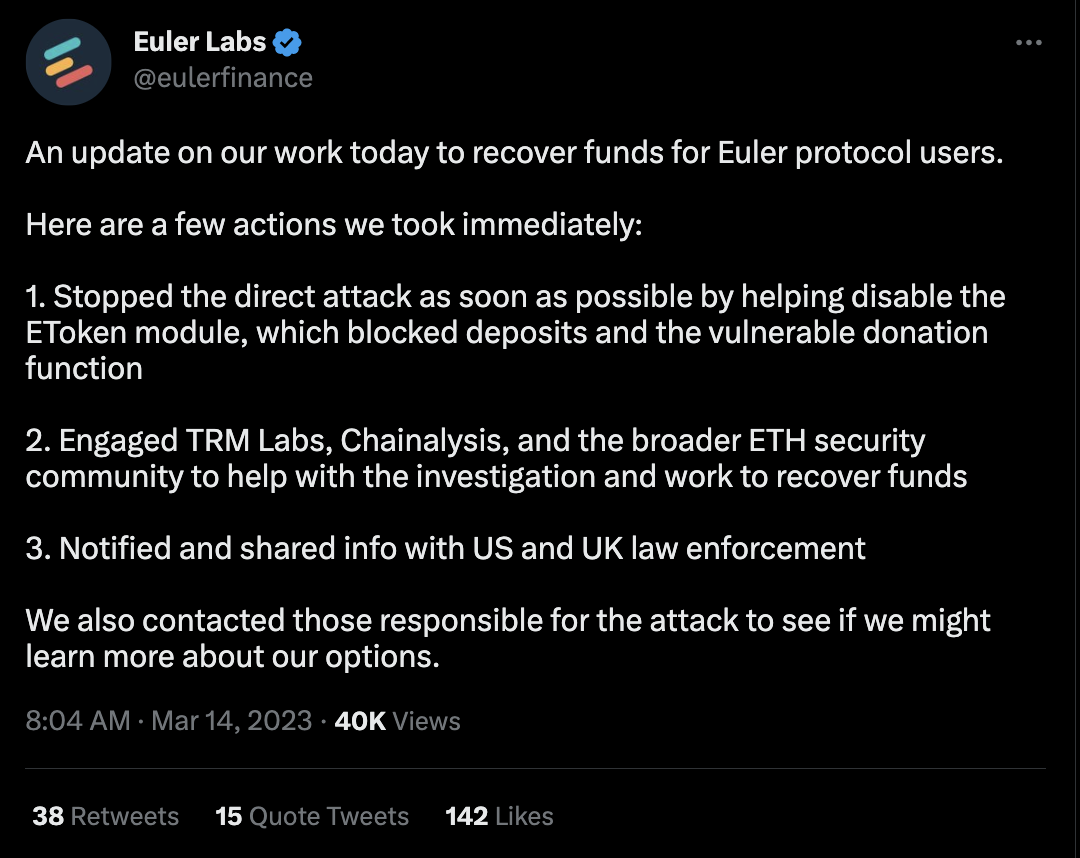
Euler Finance recently provided an update on their efforts to recover funds for their protocol users. They outlined several actions they have taken since the attack, including stopping the direct attack as soon as possible by disabling the EToken module, which prevented deposits and the vulnerable donation function.
Additionally, they have engaged with various security organizations such as TRM Labs, Chainalysis, and the wider Ethereum security community to aid in the investigation and recovery of funds. Euler Finance has also shared information with law enforcement in both the US and UK.
Lastly, the company has attempted to reach out to the attackers to learn more about potential recovery options.
Conclusion
The recent attack on the Euler Finance protocol highlights the importance of implementing rigorous security measures, such as conducting thorough audits and regularly checking for vulnerabilities.
As the decentralized finance ecosystem continues to grow, it is crucial for projects to prioritize the security of their users’ funds and adopt best practices to mitigate the risk of similar attacks in the future.


