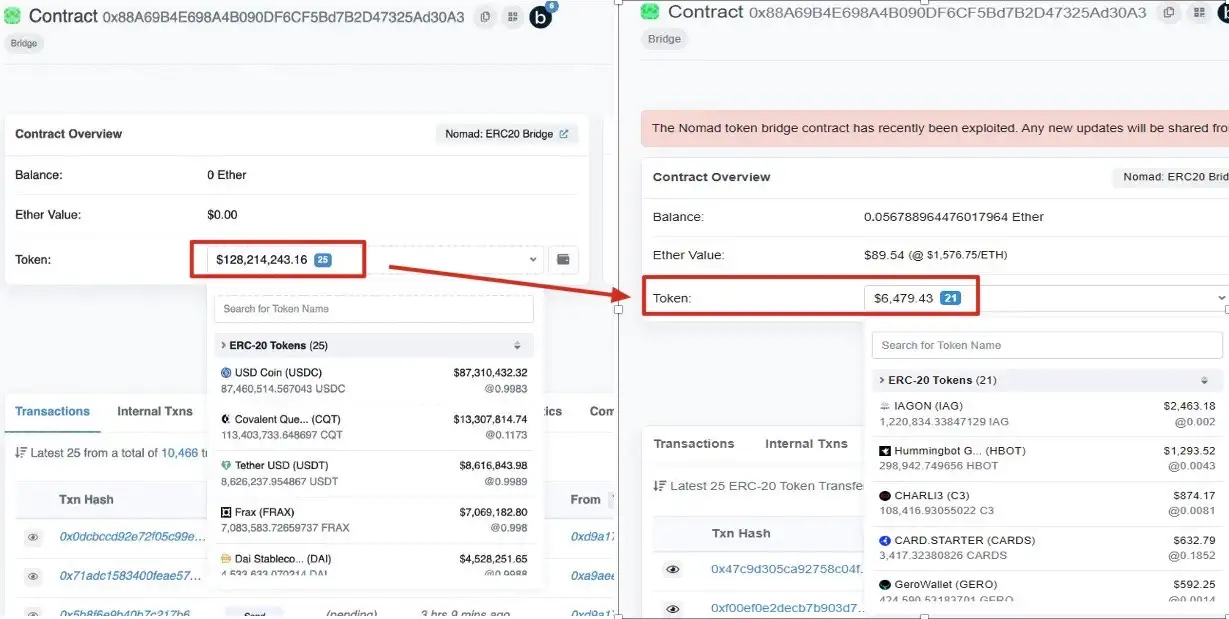
On August 2, Numen Cyber Labs monitored that the well-known project cross-chain bridge Nomad was hacked based on Twitter user @samczsun and on-chain transactions. Currently, the Ethereum cross-chain bridge protocol has gone from the original $128 million worth of assets to only $6473, the amount of loss is huge. After analysing the recent transactions, we found that the hacker obtained 10,000 ETH from the latest transaction. Next, we will give a detailed clarification about how it occurred.
Relevant Details
Nomad ERC20 Bridge Address:
https://etherscan.io/address/0x88a69b4e698a4b090df6cf5bd7b2d47325ad30a3
Hacker address:
https://etherscan.io/address/0xb5c55f76f90cc528b2609109ca14d8d84593590e
Attack Contract Address:
https://etherscan.io/address/0xf57113d8f6ff35747737f026fe0b37d4d7f42777
Attack Transactions:
https://etherscan.io/tx/0xc4938e6f6368061194d076d44f73a8cae3a318b1ee7cf8b026abe10b7c206c2a
Event Analysis
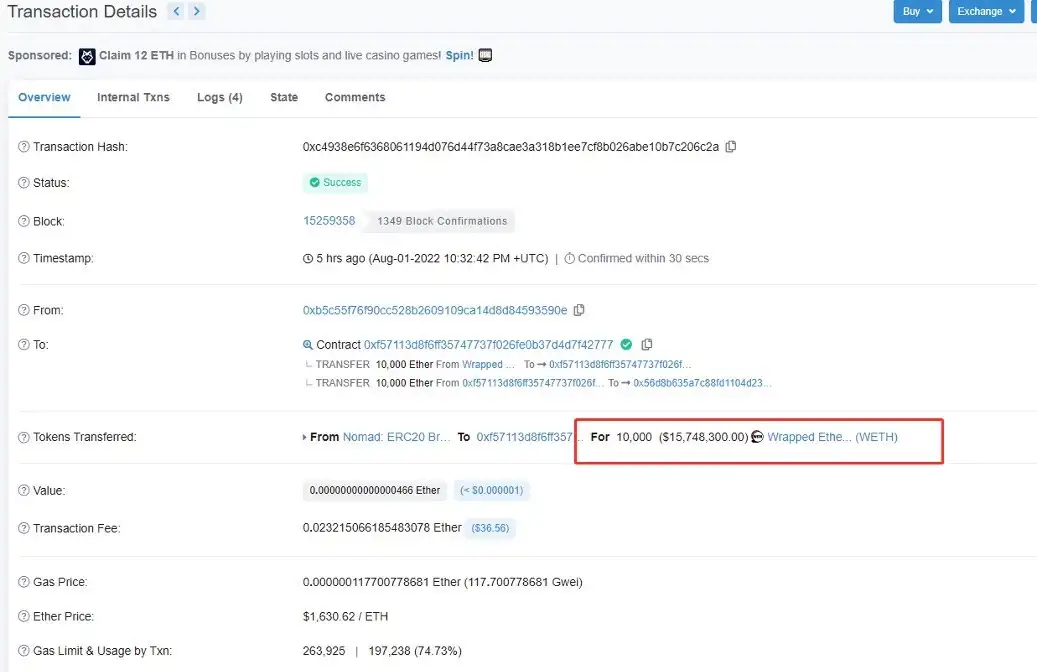
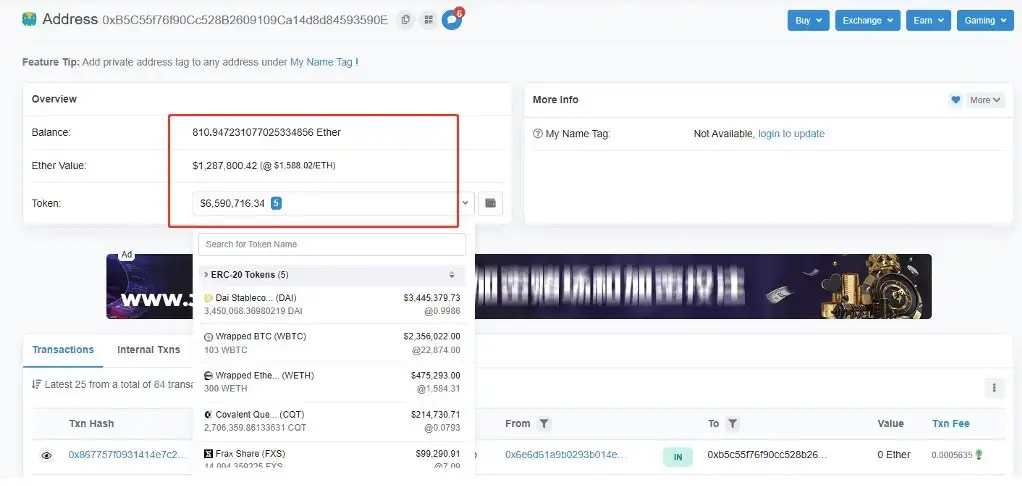
As shown in Figures 2 and 3 below, the attacker obtained 10,000 ETH under the Nomad ERC20 Bridge in this transaction, worth 15748300 US dollars. After checking the hacker’s address, we found that the hacker made multiple transactions, and the total profit on the hacker’s address was 7878516 US dollars, and the profit amount was huge.
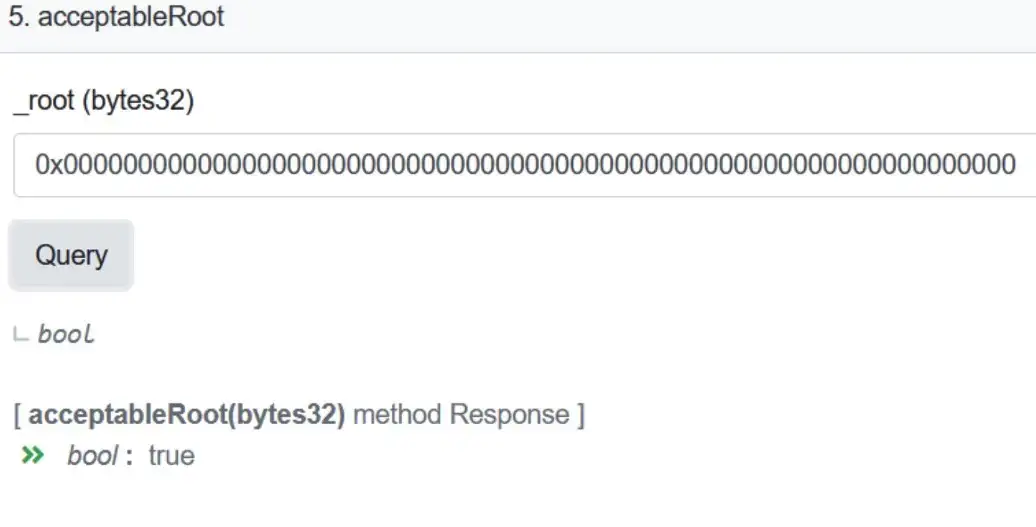
By analyzing the Nomad ERC20 Bridge code and previous initialization transactions, we found that the Nomad team marked the 0x00 as acceptable root during a previous upgrade initialization, as shown in Figure 4, and 5 below.
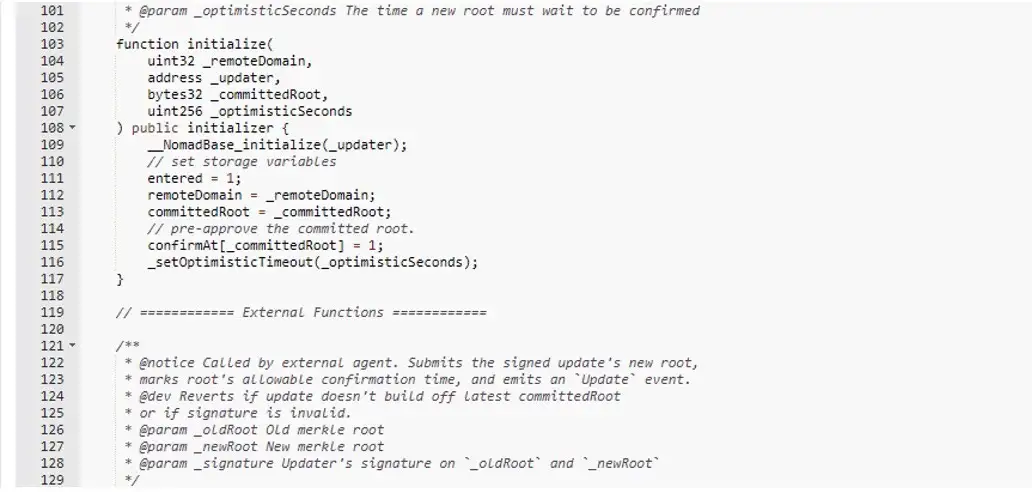
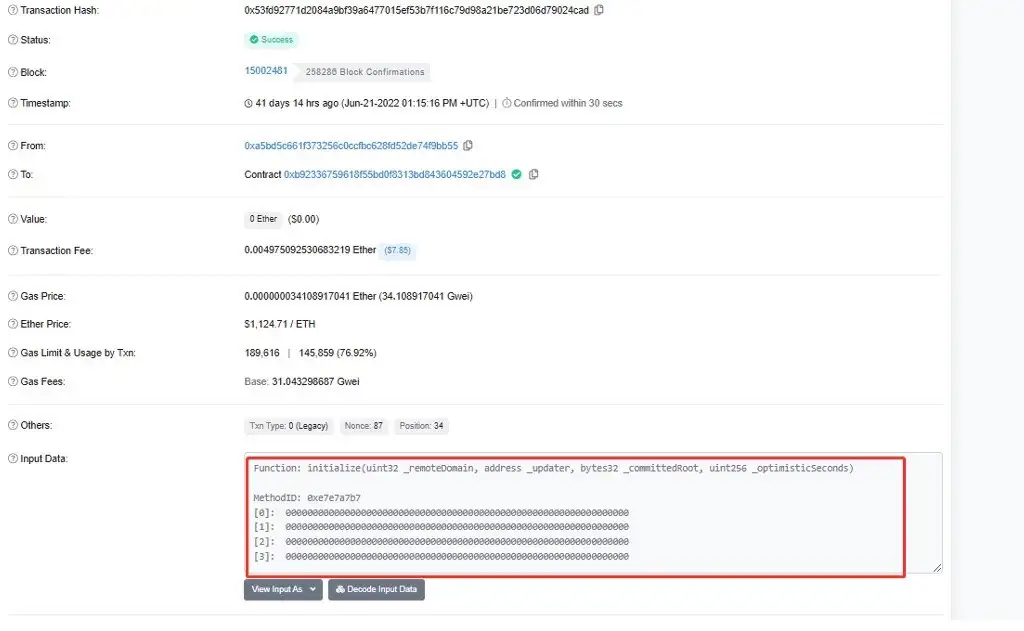
As shown in Figures 6 & 7 below, we know that the root of the unverified message is 0x00. Initially, messages[_messageHash] were uninitialized, and then the Nomad team initialized the 0x00 to acceptable root when they did upgrade, so the require function here can be verified to pass, then the attacker can forge the trust heel and each message can be validated through.
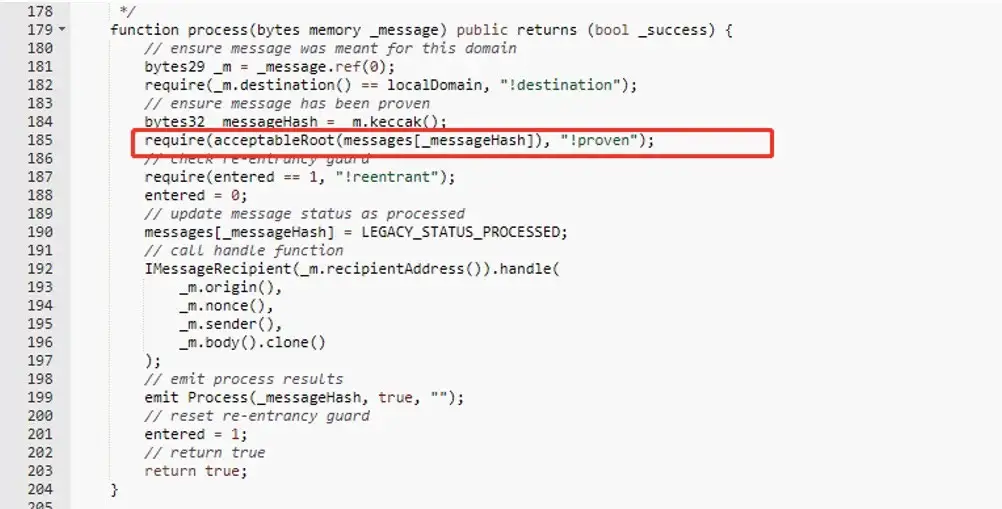
In this way, we can broadcast it by looking for someone else’s valid transactions, and then changing their address to our own address, forging a message through verification, and completing the transaction. An attacker exploits the code multiple times by calling the vulnerability multiple times and implementing multiple attacks using multiple addresses. In multiple attack arbitrage, the funds under the cross-chain bridge were exhausted.
At present, the Nomad project has discovered the attack and has also issued a statement on their official Twitter. It claims that the situation is under investigation, and the results will be released in time. Numen Cyber Labs believe that the parameters for initialization are extremely important when the contract is upgraded and deployed. And the project must be fully tested even when initializing with the default value of 0 or the default 0 address.
Conclusion
Should you wish to audit and ensure that your projects are free from exploits such as these, reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


