Event Summary
On October 2nd, Numen Cyber Labs discovered that Transit Swap, a cross-chain trading platform supported by TokenPocket, had been hacked, resulting in significant losses. The hacker’s address, 0x75F2abA6a44580D7be2C4e42885D4a1917bFFD46, currently holds 3180 ETH, worth $4,161,559 on the Ethereum chain, 49,612 BNB on the BSC Chain, worth $14,011,105, and other tokens, for a total loss of nearly $21 million.

Attack Analysis
The attack occurred on the Binance Smart Chain (BSC). When a user uses Transit Swap to exchange tokens, an entry contract (0x8785bb8deae13783b24d7afe250d42ea7d7e9d72) is used to determine the path for the token transfer. The contract 0x0B47275E0Fe7D5054373778960c99FD24F59ff52 then calls the claimtokens function of the contract 0xed1afc8c4604958c2f38a3408fa63b32e737c428 to initiate the transfer.
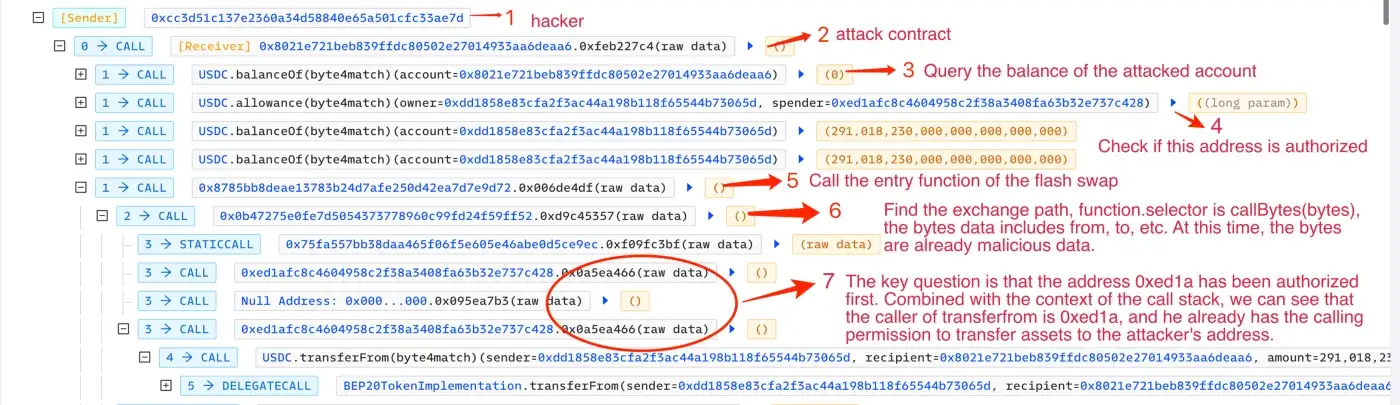
As shown in above figure, the first few calls are checking the balance and checking whether the specified contract has permission to call transferfrom.
To initiate the attack, the hacker first called the contract 0x8785bb8deae13783b24d7afe250d42ea7d7e9d72, which functions as an entry point for flash swaps.
They then used the callBytes(bytes) function of 0x0b47275e0fe7d5054373778960c99fd24f59ff52 with malicious data. They then called the getFeeRate(address, uint256, uint256, string) function of the contract 0x75fa557bb38daa465f06f5e605e46abe0d5ce9ec to check the rate.
Lastly, they called the claimTokens(address, address, address, uint256) function of the contract 0xed1afc8c4604958c2f38a3408fa63b32e737c428. This function first authorized 0xed1afc8c4604958c2f38a3408fa63b32e737c428 and then executed the transfer with different branches inside the function. The figure below shows the data used for authorizing the transfer.
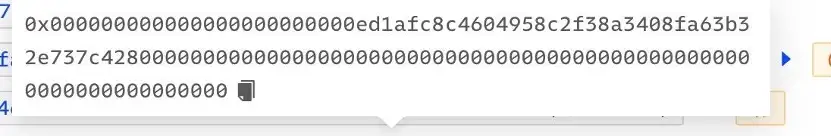
Examining the call stack, it can be seen that the address specified as the “transferfrom spender” is 0xed1afc8c4604958c2f38a3408fa63b32e737c428, which has been granted permission to call the “transferfrom” function to transfer money to the hacker’s address.
Reference TX: 0x181a7882aac0eab1036eedba25bc95a16e10f61b5df2e99d240a16c334b9b189
Summary
In the ERC-20 protocol, the process of approving authorization has long been a source of security concerns. There have been numerous incidents related to it. Additionally, when calling functions across contracts, it is important to be cautious when transmitting data from the upper layer to the lower layer. It is important to remember that the return value given by the lower layer to the upper layer must be considered untrusted and verified correctly. In a bear market, hacking incidents occur frequently, and users should be particularly vigilant.
At present, Transit Swap has suspended all contract trading functions and is attempting to track the hacker’s information in an effort to recover the stolen assets. Numen Cyber Labs suggests using revoke.cash to cancel any contract authorization and withdraw funds from Transit Swap.
According to the latest information available, the attackers have returned approximately 70% of the stolen assets.
If you wish to audit and ensure that your projects are free from exploits such as these, please reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


