
On 13 April 2023 at 05:52:35 AM +UTC, iearn Finance, a deprecated version of DeFi protocol Yearn Finance, experienced a Flash Loan Attack that led to millions of dollars in losses.
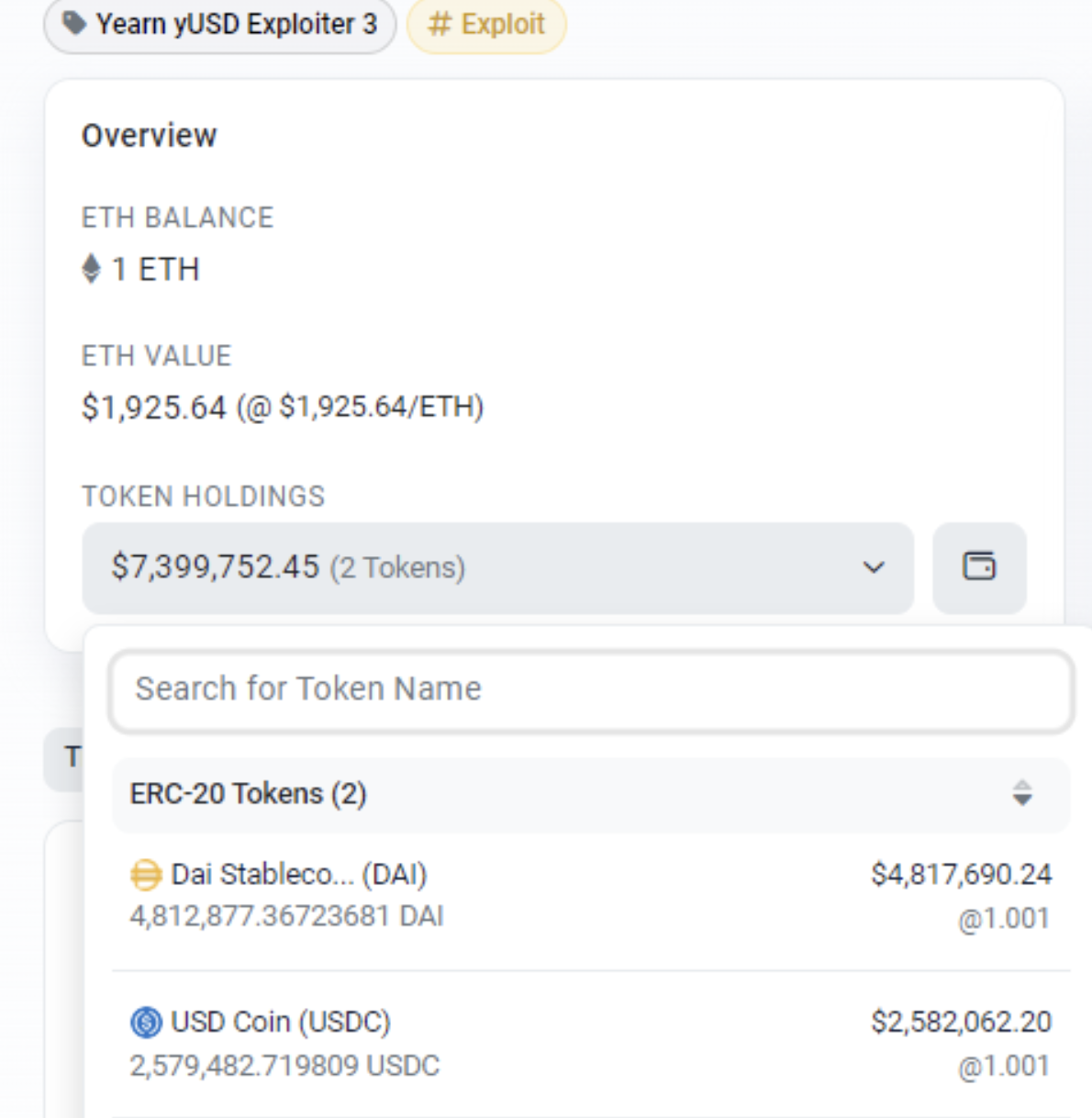
The losses that occurred on Aave version 1 could exceed a staggering $11M, which includes a range of stablecoins such as DAI (3032142), USDC (2579483), BUSD (1785091), TUSD (1512528), and USDT (1193756), amongst other currencies.
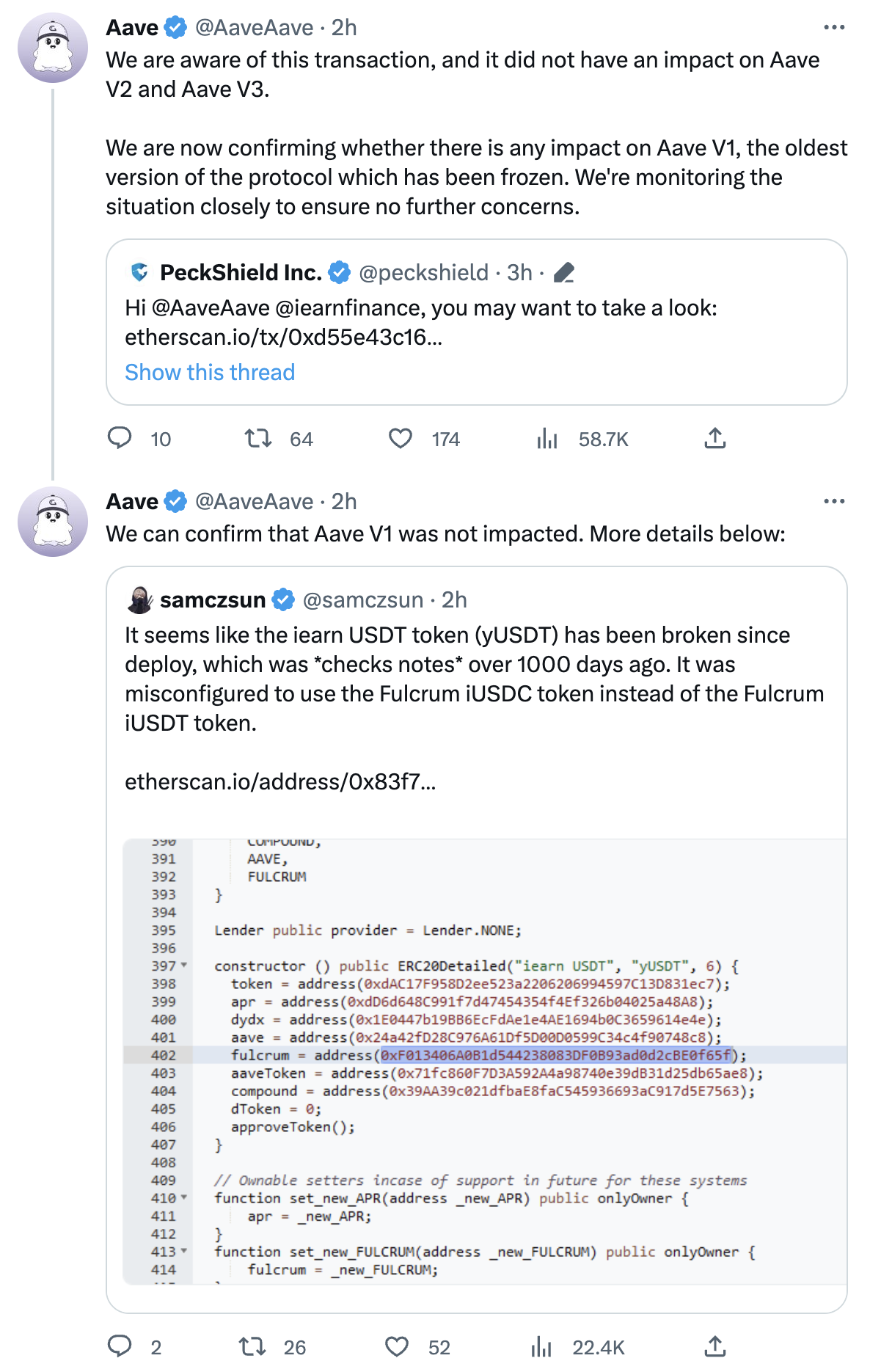
Initially, it was believed that the exploit had impacted Aave V1. Nonetheless, the developers of Aave have clarified that the protocol was not affected by the exploit, and it was only used for swapping tokens to carry out the exploit. The main stablecoin involved in the exploit was Yearn Finance’s yUSD.
Detailed Analysis
The following are the links to the hacker addresses:
Hacker address 1: https://etherscan.io/address/0x5bac20beef31d0eccb369a33514831ed8e9cdfe0
Hacker address 2: https://etherscan.io/address/0x16af29b7efbf019ef30aae9023a5140c012374a5
Hacker address 3: https://etherscan.io/address/0x6f4a6262d06272c8b2e00ce75e76d84b9d6f6ab8
Here are the details related to the attack:
Hacker contract address 1: https://etherscan.io/address/0x8102ae88c617deb2a5471cac90418da4ccd0579e
Hacker contract address 2: https://etherscan.io/address/0x9fcc1409b56cf235d9cdbbb86b6ad5089fa0eb0f
Attack transaction 1: https://etherscan.io/tx/0xd55e43c1602b28d4fd4667ee445d570c8f298f5401cf04e62ec329759ecda95d
Attack transaction 2: https://etherscan.io/tx/0x8db0ef33024c47200d47d8e97b0fcfc4b51de1820dfb4e911f0e3fb0a4053138
Attack Process
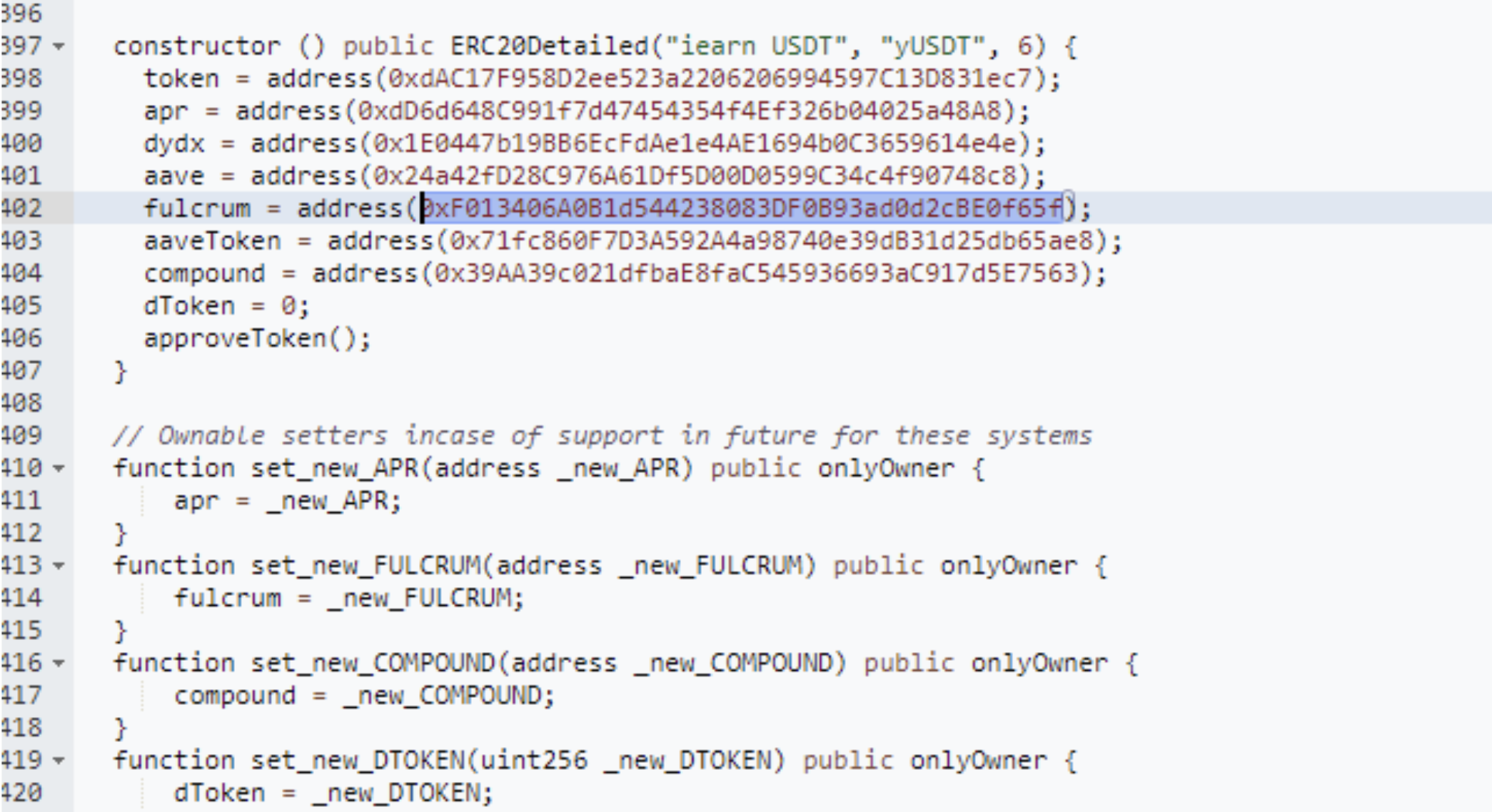
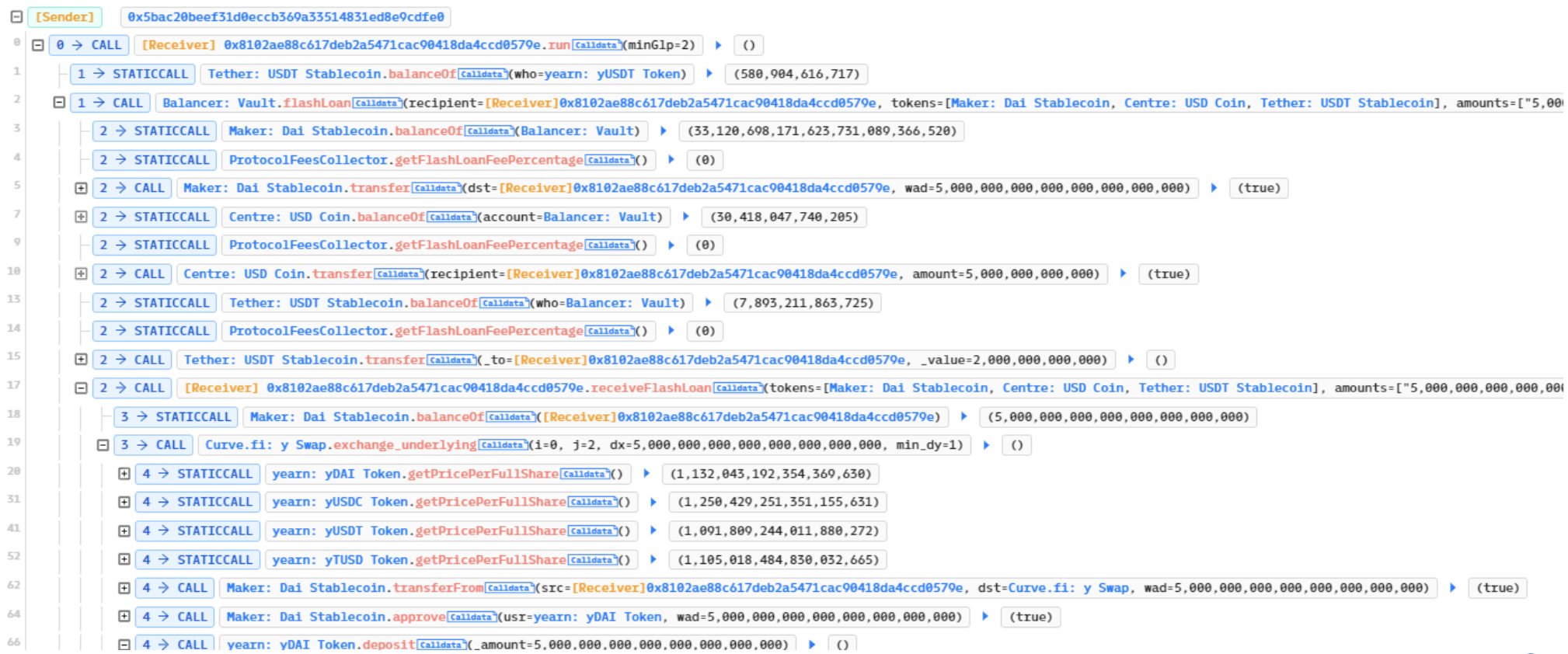
The attack was executed by exploiting a flaw in the yUSDT contract. Specifically, the fulcrum in the contract was using the iUSDC token instead of the iUSDT token, resulting in a mistaken dependency on the pool’s underlying token. To exploit this, the hacker first borrowed a significant amount of flash loans and then exchanged them through Curve to carry out the attack.
The attack involved the hacker minting bZxUSDC and sending it to the contract, which raised the price of each share. Subsequently, the hacker triggered a rebalance, resulting in the redemption of bZxUSDC for a considerable amount of USDC, causing the value of each yUSDT to plummet to nearly zero.
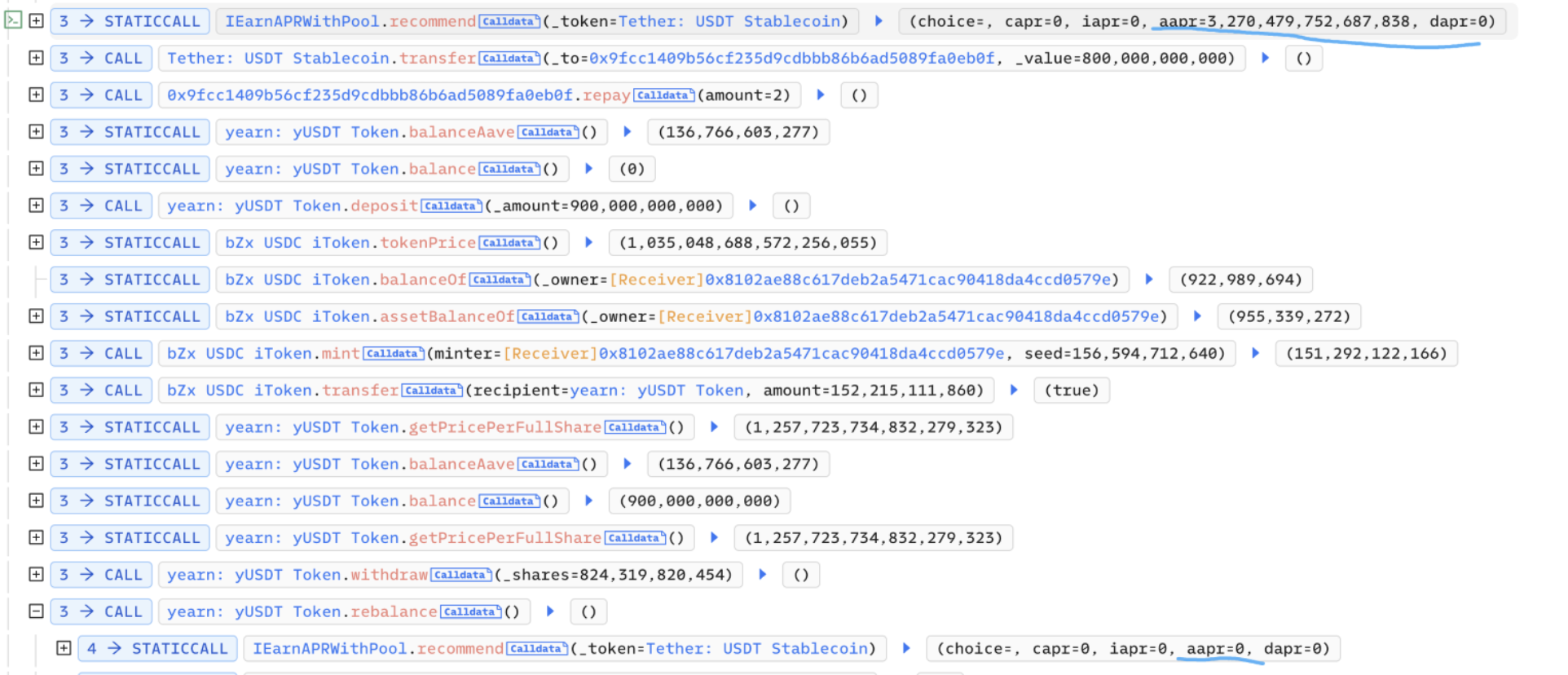
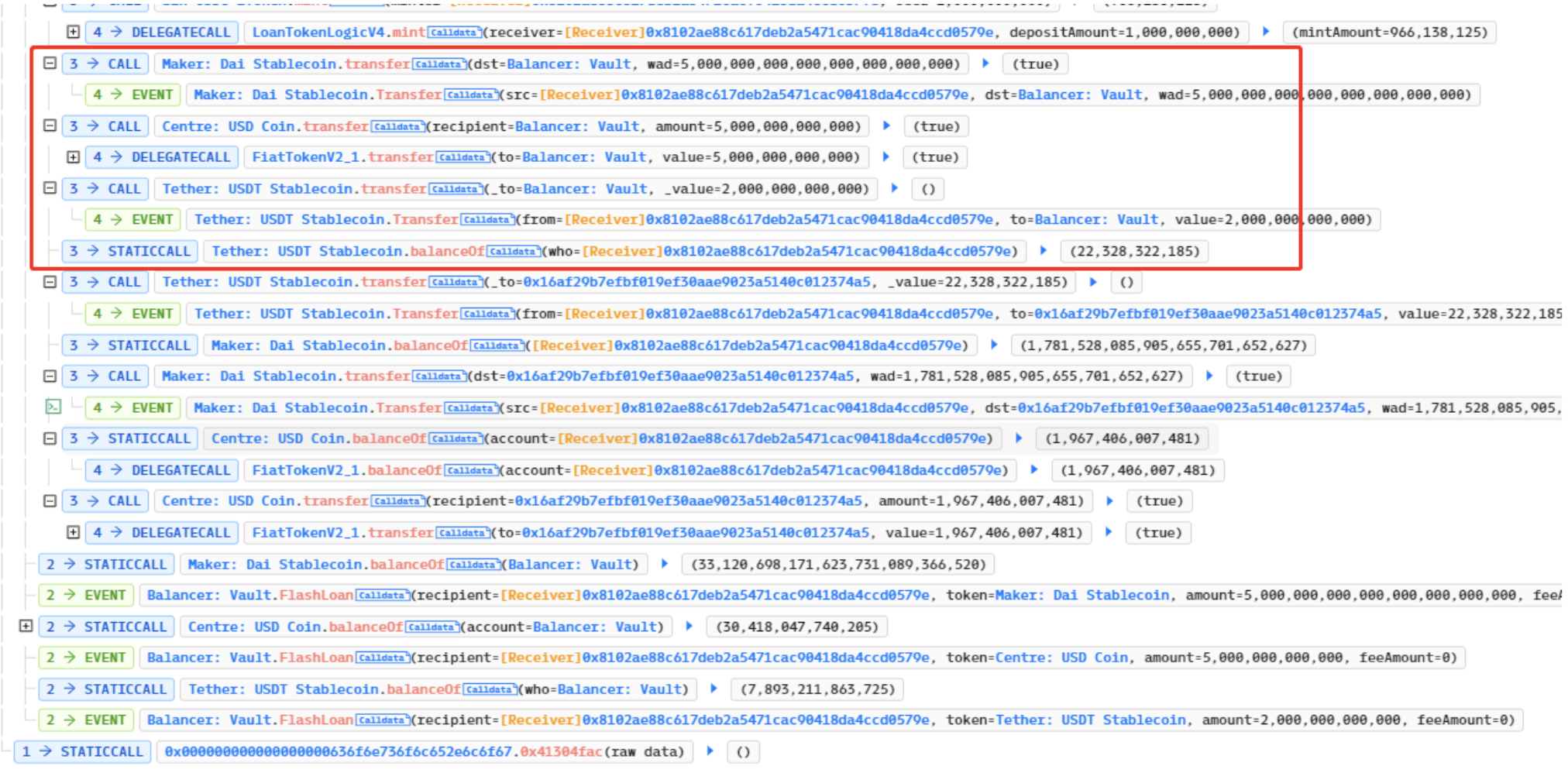
Subsequently, the hacker transferred 1 wei USDT to the yUSDT contract, which enabled them to mint yUSDT at the price of just 1 wei USDT. This essentially constituted free minting. The hacker then profited by exchanging the minted yUSDT through the Curve pool.
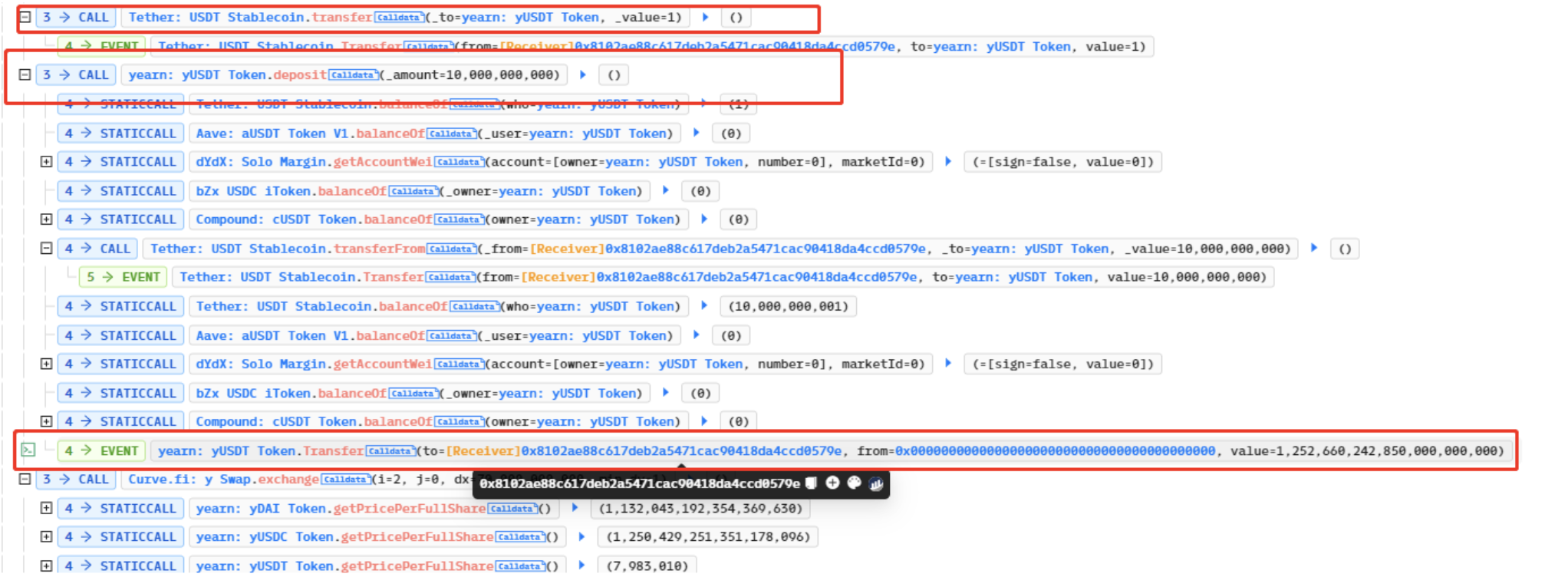
Once the hacker profited, they repaid the borrowed flash loans and swiftly exited the scene. The profits were then transferred to the hacker’s address.
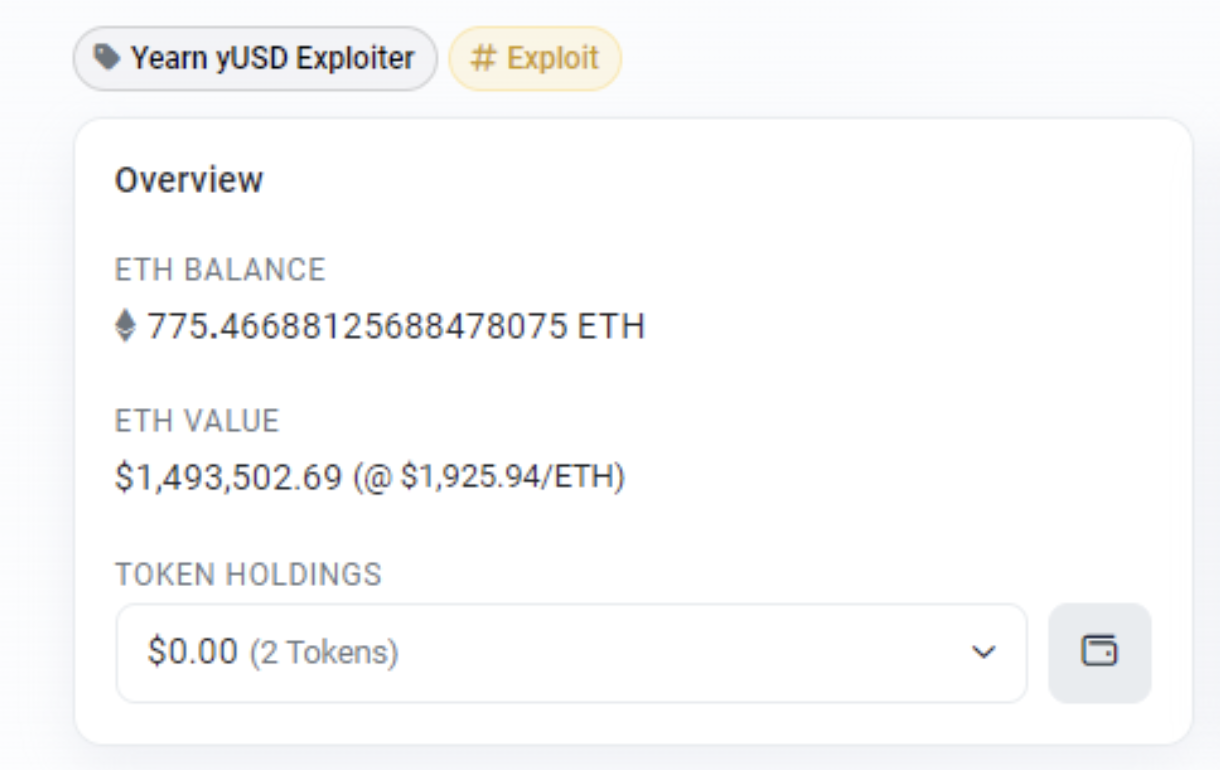
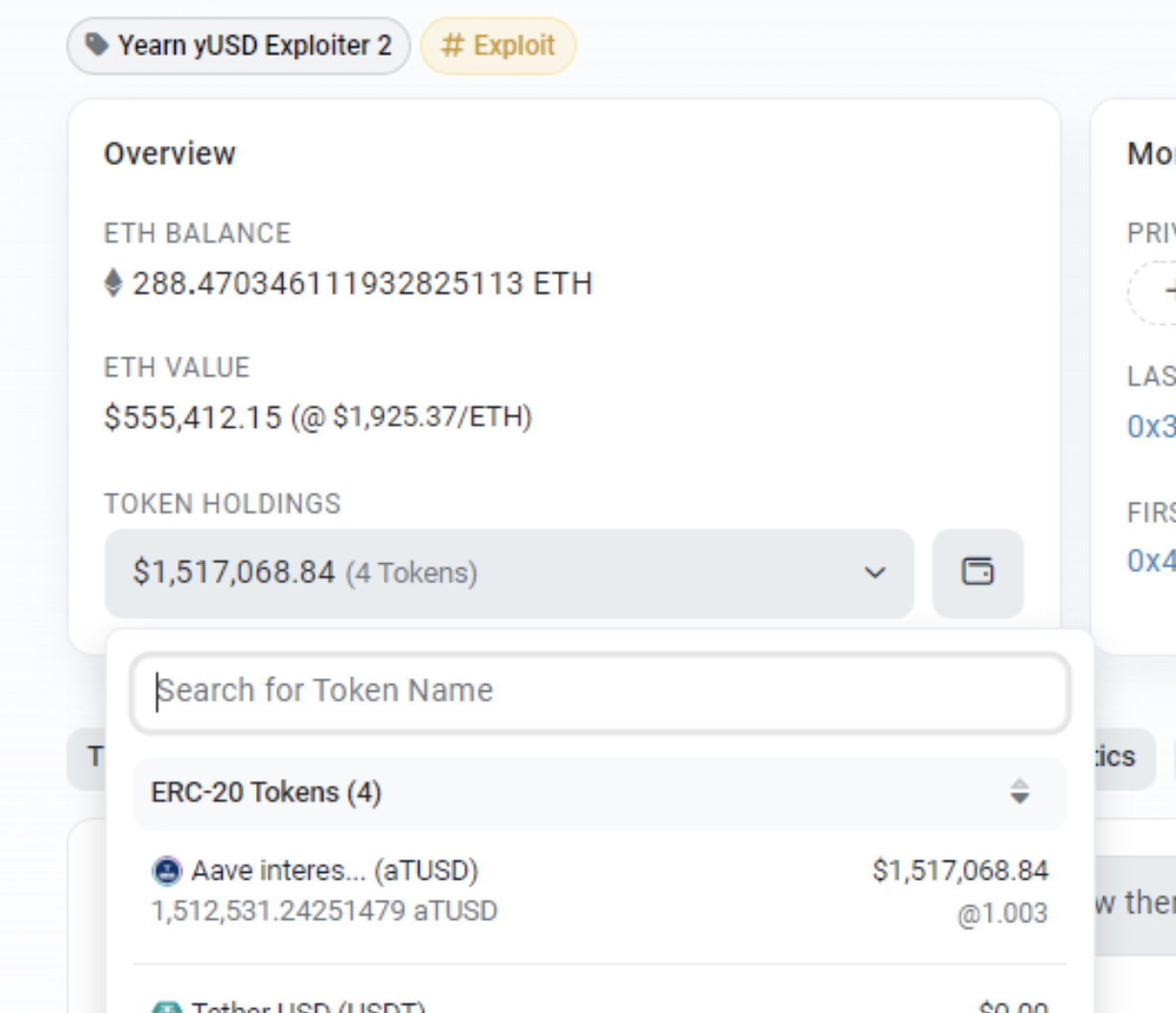
Status of Funds
As of now, the funds remain in the three hacker addresses and have not been moved. We will continue to closely monitor the situation and provide updates in case there are any further developments or movements of the funds.
Official Updates
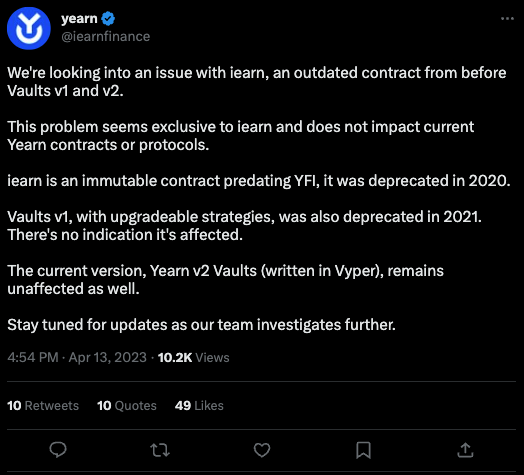
Yearn Finance has acknowledged the exploit and released a statement stating that the attack was related to an outdated contract that predates Vaults v1 and v2. Furthermore, they claim that the attack does not affect their current contracts or protocols.
At the moment, Yearn Finance is conducting internal investigations to gather more information on the attack.
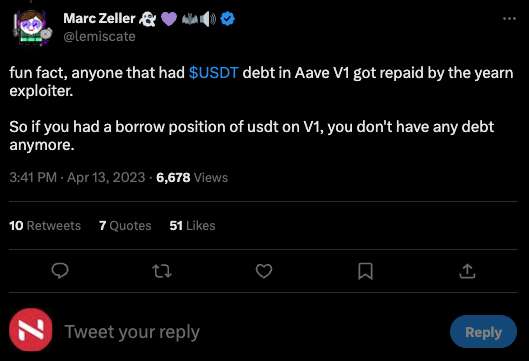
Marc Zeller, the founder of Aave, released a statement clarifying that the exploit had no impact on Aave V1, and did not affect V2 and V3 either.
Interestingly, Zeller claims that the exploit has even worked in favor of some users of Aave V1. According to him, the exploiter paid off the USDT debts of several users, resulting in them benefiting from the attack.
The attack that targeted the iearn Finance protocol emphasizes the significance of enforcing strict security measures, such as conducting comprehensive audits and regularly scanning for weaknesses.
With the decentralized finance landscape expanding, it is imperative for projects to prioritize the safety of their users’ assets and adopt industry best practices to minimize the possibility of similar attacks occurring in the future.


